Get a Lunch/Give a Lunch with One Identity: Webinar - Work From Home - Cincinnati - 4/7
We are sorry, the event "Get a Lunch/Give a Lunch with One Identity: Webinar - Work From Home - Cincinnati - 4/7" has already expired.
You may also be interested in.

AI Powered Identity: Fact or Fantasy?
In a world of deep fakes and AI horror stories, are there any benefits to using AI in something as vitally important as your identity access management (IAM)? One Identity field strategist Robert
Attend Event
TEC Talk: Microsoft Security Copilot – Potential, Hype, and Risk?
Learn to support IT organizations in strategy and implementation of security and compliance in digital transformation
Watch Webcast
TEC Talk: 5 Steps to Embark on Your Zero Trust Journey with Microsoft 365
Focus on securing identities, devices and applications, which are usually the first pillars to tackle in a Zero Trust journey. You will walk away with five projects that you can implement in your organization.
Watch Webcast
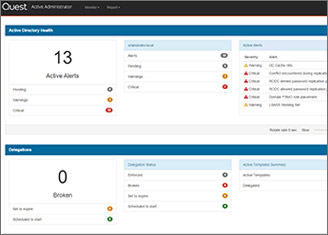
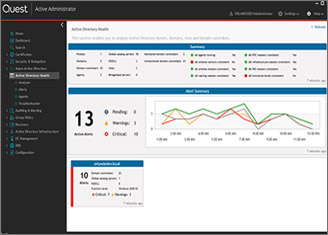
TEC Talk: Controlling the Control Plane: Defining Gaps in Tier Zero to Shut Down Attack Paths
A history of the Enterprise Access Model and why this governance model is a critical baseline for securing identities and resources.
Watch Webcast
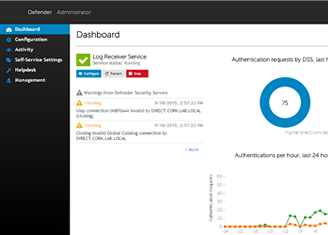
TEC Talk: Proper Password Protection within Active Directory and Azure Active Directory Environments
Attacks against Active Directory have been steadily increasing in the last few years. What is needed for proper password protection has changed.
Watch Webcast
The Future of Your Group Policy GPOs
Group policy objects (GPOs) are essential to the security and management of your IT environment, but they are often challenging to manage. Perhaps you've been using Microsoft Advanced Group Policy Man
Attend Event
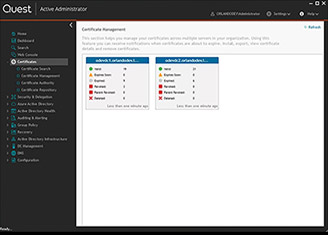
Modernizing security: Proactive PAM solutions for today
One Identity Cloud PAM Essentials is a SaaS-based privileged access management (PAM) solution that prioritizes security, manageability and compliance.
Read E-book