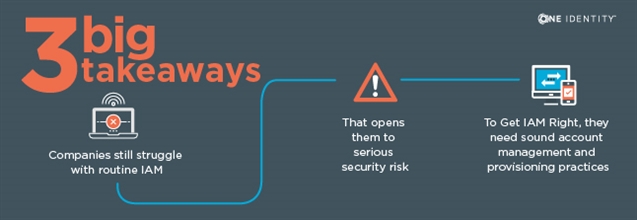
We’ve all been there – you’ve been doing something the same way for years and it seems to be going well. You’re in a groove and everything happens like clockwork. You know exactly what you’re doing and the results are predictable. You’re a well-oiled…