Hi,
I have a test employee with same accounts in both v8.0.1 and 8.1 environments.
If I change the password via Portal I've noticed the following behaviour:
- In v8.0.1 the password change affects all password items including centralpassword.
- In v8.1 the password change does not affect the central password.
Digging deep in the code:
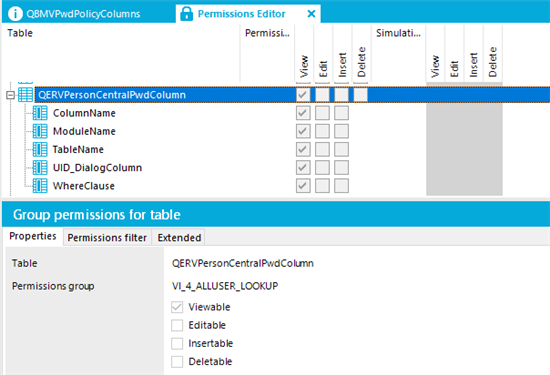
The PasswordItem collection in v8.0.1 fills up with all accounts and passwords for the user, included the CentralPassword (Person account) and DialogUserPassword (Person account)
The PasswordItem collection in v8.1 fills up with accounts , but for the Person account will only fill up with the DialogUserPassword and not with the CentralPassword.
No customizations are done. QER\Person\UseCentralPassword\SyncToSystemPassword is checked in v8.1
If I try my own user, then it works fine in both environments (¿?). Then I went to another employee and found the same behaviour as for my test employee: Only the DialogUserPassword in v8.1
Am I hitting a bug or is there something in the Person object I should check ?
Regards!