We've switched a couple of times in my tenure between expensive and complex encryption products ... moving from one hot mess to another.
They get the job done, but each baby comes with it's own special formula and brand of diaper.
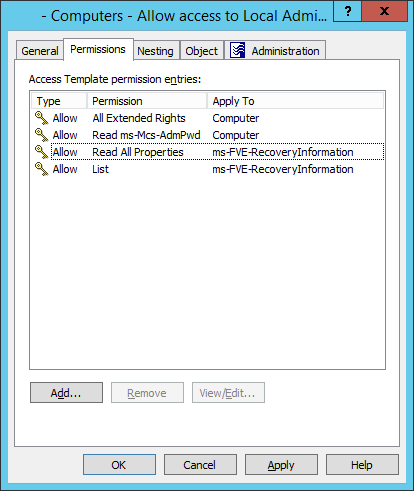
Now, we're looking at Bitlocker. I've been asked to provide information on what ActivRoles features are available for managing access to bitlocker information for our helpdesk. This forum has some posts, but nothing useful written in this century. Does anyone use bitlocker in their environment -and use ActiveRoles to provide delegated access to host keys etc? Do you have a link to additional quality information about how/what ARS provides along these lines.
I see the link in the web interface(s) ... and have followed the rabbit trail there, but I'm looking for some reading material.... or advice.
thanks