We have a normal user with only domain user access rights. These users can manage their own AD groups, e.g. they are primary managers of an AD group.
While logged in via the selfservice portal as a normal user, we click on the "Groups I manage" within the portal and it show my groups.
Looking at the web browser URL, I can change my name, e.g. bob+jones to beth+hope, and hit enter. It then shows me the other users groups they manage and I can at that point add or remove people from those groups.
Example URL: server/.../CustomCommands.aspx
I should not have the ability to change any group that I don't manage.
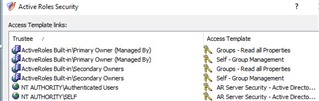
Within Active Roles console when logged in as admin, I'm able to see the history for that group and it shows me that my normal account made changes to the group I shouldn't have access to.
Is this something others can do or is it my console/web configuration?
Is there away to run a report to show all groups that have been changed by users that don't have primary or secondary management?