Provisioning.
Workflow.
Policies.
When these words come up people suddenly have a thought in their mind defining its meaning. Many Identity Management products sound the same, One identity even has multiple products that may use the same words to describe its functionality. However, when you understand the context, these words have a different meaning.
Provisioning
Automation comes to mind when I hear this word. When dealing with an Identity Management system, I am typically dealing with automation of the creation of user accounts or removal of access based on data from the Human Resources department. Defining what actions should occur when you are creating or removing access requires coordination between people from different departments. Deploying an Identity and Access Management solution can be a time consuming process, not always due to the technology that exists, but in the creation of policies to determine what should occur. When dealing with Active Directory, provisioning still occurs when admins create accounts or grant access OUTSIDE of their Identity solution as they still have direct access to Active Directory. I haven’t met a customer yet that has defined every possibly scenario that could occur and defined that situation with their Identity Management solution. Even if this was desired it would be cost prohibitive with the amount of custom development with their Identity Solution for actions that may never occur (and as situations change this would be a never ending development cycle).
One Identity offers Active Roles, which provides a simple provisioning solution that can read data from a text file and automatically create or de-provision against Active Directory. Whereas Identity Management solutions typically will work across multiple systems, we are focused on Active Directory. Also, even if you have an Identity tool performing this function against Active Directory, we can still implement provisioning capabilities when people are making changes directly to Active Directory. By using our product you can control what is changed with Active Directory when people are making changes outside of their Identity Management product. This can all be done with configurations, no coding experience required.
Workflow
Humans are involved when dealing with workflow. Typically someone should approve something prior to something else happening. Identity Management tools use workflow to bring the business into the decision making process. Dealing with the business and defining the workflow can be a challenging ordeal. Identity tools provide an interface that non-technical people can adopt to approve or deny requests for items that they should provide a decision for.
As stated before, people still make changes OUTSIDE of their Identity tools. When admins make changes directly in Active Directory, Active Roles can provide workflow for those changes. So before adding someone to the Domain Admins group, multiple people may need to approve that. If using Group Policies (I haven’t heard of any Identity Management tool that manages this), Quest has GPOADmin that can have workflow so that prior to making a change that can affect every person in the organization can have multiple levels of approval. Unless you have removed all administrative rights to Active Directory, people still have rights to Active Directory and Quest can provide workflow capabilities for those systems.
Policies
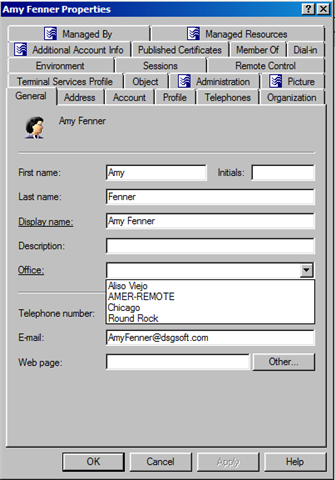
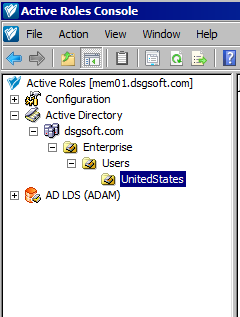
What should people be allowed to do? Identity tools can help with policies across multiple different systems. One Identity has solutions to provide policies where only groups (and not individuals) should be granted access directly on a NAS device as an example. However, when people are given the ability to have direct access to Active Directory this becomes more challenging. I do not know of any Identity Management tool on the market that does least privilege access of Active Directory. Active Roles helps enforce your least privilege access policies so you only see what you should be allowed to see. We also provides policies so you can only populate attributes in a specific way. This ensures you have data consistency in your environment and can even work with dynamic groups based on attributes being set in a certain way (Active Roles provides a lot of additional group management functionality).
Figure 1: Example policy for admins where you have a drop down box for selections.
Figure 2: Delegation configured so user can only see what they have rights to.
Active Roles provides a lot of capabilities that can complement any Identity solution. There are some similarities, but a lot of additional value that makes it a choice to consider for any organization. Some organizations may even take advantage of the text file provisioning as a band aid for immediate relief to buy time to define and implement other Identity tools that connect to additional systems.