Back to basics—understanding directories and privilege.
Directories, particularly your Microsoft directories, are where it all starts. Active Directory and Microsoft Entra ID (formerly, Azure AD) contain accounts, computers and resources that form the cornerstone of your IT security infrastructure. At One Identity, we are speaking with more and more organizations coming to the realization that Active Directory, however "legacy", is more crucial than ever. Some are even saying they now see Active Directory in the same light as Mainframes: it is not going away anytime soon. The challenge for IT Security professionals is to ensure that Active Directory security and protection remains fit for purpose. The observation is not an abstract one—how many AD compromise reports you can find in two minutes of googling? All the more relevant bearing in mind that Active Directory and Microsoft Entra ID are joined at the hip and any security weakness in one can quickly leak into the other.
If an account with access to your directory is compromised, it’s the start of a slippery slope. Lateral movement and privilege escalation can lead to a compromised administrative account, and then it’s game over.
So, securing your directories is a no-brainer, but in this article, we’re going to invite you to shift your perspective on how to approach securing your directories.
When is a duck not a duck?
When you look at this image, what do you see?
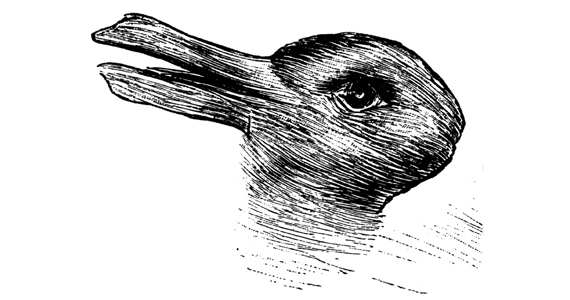
Flap or bounce?
Microsoft Entra ID: When is an account not an account?
When you look at a directory account, what do you see? Is it a store for attributes or does it facilitate authentication? Is it a login account for a business user? Maybe it’s a login account for a computer or an infrastructural component? Or maybe it's better to see it as an authoritative source for user profile attributes? Or again, it might be an account for an administrative user for the directory itself or for directory connected systems or applications. If it’s an administrative account, is it a global administrative account or is it scoped to manage a subset of resources?
Of course, we can see that these are all accounts, but we need to look at them in a particular way to appreciate the risk and security obligations they imply.
Let’s continue to squint at the directory.
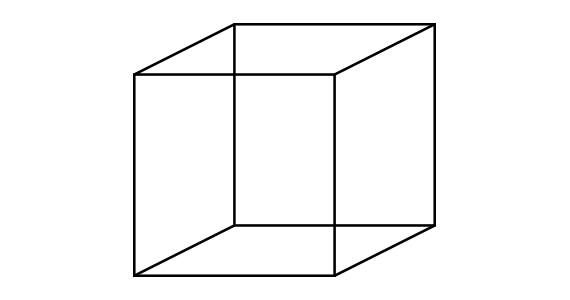
Necker cube: down to the left or up to the right?
Microsoft Entra ID: When is an attribute not an attribute?
It’s clear that firstName, givenName, description are simple attributes. But what about userPassword? Passwords are special, aren’t they? They have a particular syntax, behaviour and supporting workflow. So, one answer to the question is, “An attribute is not an attribute when it’s a password.”
But what about member for a group membership? Memberships are special, aren’t they? They confer directory, system or application entitlement, or privilege on the holder of the account credentials.
And what about title, the job title attribute? This does not directly confer privilege, but it may be an entitlement carrying attribute. So while it is an attribute, we need to understand it as being more than that from a security point of view.
And so…?
Securing your directory estate requires appreciating the different facets and security risks associated with directory objects. Every account and attribute in the directory has some level of entitlement and privilege attached to it, creating a spectrum of security obligations. The most complete and effective security strategy for your directory estate starts from this viewpoint.
Does that mean every Microsoft Entra ID: account is a privileged account?
Yes! It’s a question of degree. All accounts have privilege associated to them, and this makes the problem of securing your directories a problem in Privileged Account Management. Looking at it this way means you are starting with the right mindset to achieve a robust and resilient security stance for your directories. In the following section we’ll test this idea against specific use-cases.
Privilege Driven Security Policies for Microsoft Entra ID
Shifting our perspective on directories to privilege leads us naturally to a Privileged Account Management (PAM) style approach and allows us to benefit from well-established PAM best practices and methodologies. You will need some tooling to help with this and for a full defense in depth protection you may lean on several technologies. We will explore these options in this section.
What about Least Privilege?
Exactly! Now that you see that your problem is to manage privilege, you will want to drive down the privilege levels to the smallest possible level. This minimizes your attack surface and makes your job of securing the directory easier.
One Identity Active Roles takes Least Privilege seriously: it ringfences the directory and no one has any rights that are not conferred by Active Roles, either by policy or by request. Centralized, event-driven workflows ensure enforcement of the policies, and fine-grained delegation allows scoping to OU and attribute levels to achieve a fully Least Privilege stance.
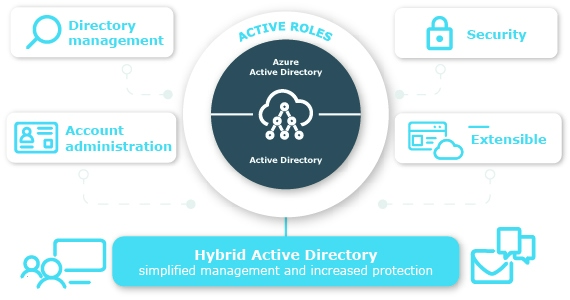
Ring-Fencing the Directory
Just-In-Time Access (JIT)
JIT takes Least Privilege to the logical limit of fine-grained control by taking the approach of only elevating account privileges to the point they are needed. By reducing the time frame within which the account is decorated with powerful entitlements, it significantly reduces the risk of privileged credential compromise and abuse. The Active Roles Extension for Privileged Passwords combines Active Roles and Safeguard to provide JIT for privileged Active Directory accounts and ensures that those accounts are only endowed with their privileged entitlements for the period for which they are actually needed. This is a huge win in terms of attack surface reduction and corresponding risk reduction.
This diagram provides an architectural overview of how Active Roles and Safeguard cooperate to achieve JIT privilege control:
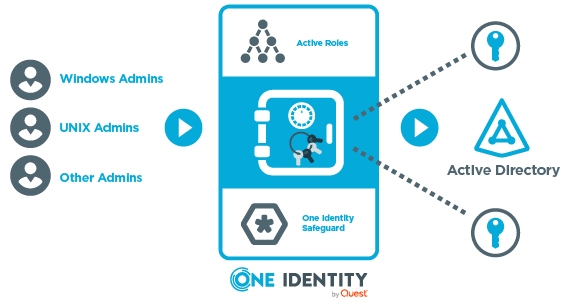
JIT Architecture with Active Roles and Safeguard
Please refer to the references for a friendly video walking you through Active Role’s JIT privilege elevation capability.
Delegation of Administrative Control to the Directory
Delegation of control in a PAM context needs to be centrally controlled by policy and should follow a Least Privilege model—it cannot be an ad hoc affair. However, in older Directories or in highly fragmented Directories that have evolved over time due to Mergers and Acquisition activity, it can be a real challenge to adhere to those well-known good-practice principles.
Active Roles solves this problem from start to finish. Firstly, in a fragmented state it allows you to centralize the access policy for the whole estate, consolidating the directories to provide unified, fine-grained and specific access to just the right administrators. Over time you will (hopefully!) consolidate your fragmented Domains into a core reduced set of Domains or even to one single Domain. In a way you now have the opposite problem: how to divide up the logical access to the directory. Well, Active Roles solves this problem in a similar way, but now rather than bringing resources together in a logical way, it is separating them logically through fine-grained access control policies.
Active Roles is the software that keeps on giving, bringing value at all stages of your journey towards a well-managed, secure directory!
Multi-Factor Authentication (MFA)
A PAM approach to securing directories implies MFA for any administrative activity.
One Identity is fortunate in being able to offer not just One Identity Active Roles for securing the directory, but also several supporting solutions, like MFA, to reinforce the authentication for those privileged users. We offer this through OneLogin, which also brings SSO or via One Identity Defender.
Monitoring and Auditing
If something important is happening, we’re going to want a record of that.
I got a work call one Sunday night during an AD migration project complaining that “my product,”— Active Roles, as it happens— was “doing something weird”. Simply by looking at the Active Roles audit log, we could see that one of the customer admins had logged in and made changes. Off the hook, but more importantly we now had a clear indicator of how to remediate the issue at hand.
When you take a PAM view of the world, you will automatically consider Auditing a must-have capability.
Password Management
We already mentioned the special nature of the directory password attribute. Apart from the usual directory-based password policies, we may wish to reinforce password security for the directory by providing additional “Forgotten Password” workflows or by vaulting some of the passwords within a hardened secure appliance. Good candidates for vaulting are, for example, the administrative accounts for Domain Controller machines and Domain Admin account passwords.
Again, One Identity customers benefit from a one-stop shop for these capabilities with Password Manager and Safeguard for Privileged Passwords.
Session Management
We discussed the importance of auditing administrative actions within the directory, and Active Roles provides comprehensive audit logs for all actions. When it comes to managing the infrastructure for your directories, like the machine on which your Domain Controller is running or the administrative interface to Azure, you may wish to add additional auditing at the session level. This brings several advantages: it acts as a deterrent because people know their actions are fully recorded, and it offers an accelerated remediation path since there is a precise record of what actions were carried out.
Once again, One Identity can provide this capability with One Identity Safeguard for Privileged Sessions.
Conclusion
Active Roles, an AD and Azure AD security and administration solution by One Identity, manages privileges across AD and Microsoft Entra ID with a single pane of glass at an attribute level granularity delegation model.
Taking a PAM perspective on securing your directories leads you naturally to an approach that follows good security practice and yields excellent security posture.
One Identity is uniquely placed to assist you in adopting this PAM driven approach to directory security. Our experience in the domain, our market-leading portfolio of products and our close relationship with Microsoft ensure that we can accelerate your journey to a highly secure and resilient directory estate.
We will wrap up this article by underlining a business perspective on directory security: another Cybersecurity job well done is an excellent result, but let’s not be shy about the business impact and value that we gain. Beyond allowing our business to evolve digitally in a secure way, additional business protection is facilitated by reducing the barrier to adequate Cyber Insurance coverage. Our experience is that questions like “How many Domain Admins do you have?” are among the first questions the insurance company will ask, and this quickly slides into questions around PAM controls. As well as this business enablement dividend, the PAM approach to directory security can easily embrace other domains of the IT estate, for example by using Directory Bridging and *nix based privilege tooling that are built on the secure PAM based directory foundation.
Although securing your directory should be a no-brainer, the breach and leak statistics show that many organizations are struggling to provide adequate protection for their directory-based resources. We hope this tour has given you some new ways to think about securing your directories, and we'd be happy to help you explore this further.
References
- One Identity Active Roles Customer Success Stories
- One Identity Active Roles product
- JIT Privilege Elevation with Active Roles and Safeguard on the One Identity YouTube Channel
- One Identity Safeguard for Privileged Passwords and Sessions
- One Identity Safeguard Security Suite for Unix/Linux
For more information on how Active Roles can help you locate and safeguard your privileged accounts, visit Active Roles (oneidentity.com).




