Do your house guests still have access to your home after they’ve left, or overstayed their welcome? No, right? You would throw them out or take the keys back because they no longer require access. Guests in Azure are like house guests. Once they no longer need access, it's then time to take back the key so they no longer have access to the company's data and connected apps. Yet many organizations are inadvertently leaving themselves at risk of supply chain attacks.
Let’s start at the beginning…
The tools which we use and have at our disposal today have made collaboration much easier, with both internal and external parties.
Platforms such as Azure AD and Teams allows us to extend beyond the borders of an organization, allowing for a project team to consist of members from external organizations, sharing ideas, data and applications to work towards a common goal.
I’ll take my current role in One Identity as an example. We collaborate with clients and partner organizations using tools available within Microsoft 365 and Teams as part of joint projects. At One Identity, like many other organizations and industries, we invite external users (Guest users) to our organization to collaborate with us in MS Teams, sharing data and app access.
Gone are the days where it took weeks to provide access for an external user, raising service desk tickets, approvals, and waiting for an account to be created. Today, anyone in the business can simply invite a guest, whether it be from Teams, SharePoint, or directly within the Azure AD portal. A big win for end user productivity and user experience.
However, what happens with these Guest accounts when the project is complete, and the access is no longer required?
And here is the issue
Inviting Guest’s to an organization has become so simple to do that just about anyone can do it. But how many people inform their IT when that Guest is no longer working in the project and the access should be revoked?
In a recent project, I performed a search within the Azure AD tenant and found this organization had 5,000+ active guest accounts, all of which have been assigned permissions and access to data, shared folders, Teams, and other resources within Azure and connected to Azure AD.
There were more Guest accounts than employee accounts in this Azure environment. The next concern, there was no possible way for an IT admin to identify if any of these Guest should continue to retain their access. Some had logged in recently, however many appeared to not have authenticated for over 30 days.
Think of a scenario where you invite a trades person to perform a maintenance task on your property. It might be for repairs, backyard makeover, or kitchen renovation. You might give them the spare key, or an access code, to enter your premises to perform the work. After the trades person has completed the task, you would then revoke their access by taking back the key or disabling their access code on the security panel. We don’t want people to have access to our homes once they no longer need access.
Guest accounts in Azure AD need to be treated like guests in our homes. Once the task is complete, their access should be revoked.
Whose responsibility is it to manage Guest accounts?
In the example shared, the IT admin team had no method to identify if any of these Guest accounts were still needed or collaborating on a project. IT are not always aware, and often the last to know, of projects and business activities. As the business user’s inviting the guests to collaborate, the responsibility should lie with the business, not with IT, to ensure these accounts are removed once the access is no longer required.
The problem though with Guest accounts in Azure AD is there is no simple method for the person who had invited the guest to later revoke the access.
I performed an experiment recently to test this theory by inviting a Guest to an Azure organization, and a few days later I went back to the Azure portal to revoke the access (delete the account). It turns out that deleting the account is not possible unless you have administrator level access to Azure AD. Granting administrator access to all business users is obviously something you would not do. The only method left was to contact the administrator by raising a helpdesk ticket for the guest account to be removed.
That brings me to the next question to consider. How many people who had invited a Guest, would later raise a helpdesk ticket to revoke to the Guest’s access?
What happens in the real world
Here is where it got interesting. I went back to this client, contacted the IT admins and asked them this very question. Since the introduction of Azure AD in the organization, it appeared that not one Guest account was ever revoked. Upon further investigation, we then found that there were Guest accounts that were created in 2016, who had not logged in recently, yet remained active and retained access.
Where’s the risk here?
In a world where security breaches have become common place, cybersecurity teams are constantly challenged with evolving threats which attempt to exploit vulnerabilities and testing their defenses. Over 50% of cyber incidents reported in the NDBR for July-December 2022 were linked to a compromised credential. Recently published data breaches have found the source of the breach was a third-party’s account which was exploited their access to an organization’s applications and data.
By leaving the Guest accounts unchecked, organizations are inadvertently leaving themselves at risk of supply chain attacks which exploit third-party access to applications and data. You wouldn’t leave a set of your house keys or access to your property with the tradesperson after they’ve finished the task, yet many continue to allow Guests to retain access long after the tasks are complete.
Let’s get your keys back
If we consider Azure as the home of your (IT) organization, when an unwanted Guest no longer needs access, it’s then time remove their account.
Native tools in Azure provide some capabilities to manage Guests, but these tools are designed for the IT admin users. For example, using PowerShell scripts or the Azure Admin Portal. However, this approach assumes that IT is not only responsible for disabling access, but also is to know when the business no longer needs the guest to retain access. It places the burden on IT to keep track of every business project or activity.
Businesses need to consider a method which empowers and places the responsibility on the end users who had invited the Guest account, and ask the basic questions in identity security:
- Who – knowing who it is that has access
- What – understanding what data and apps they have access to
- Why – should this person be assigned, or continue to retain, this access
In the latest enhancements of Active Roles, an AD and Azure AD management and administration solution by One Identity, managing guest accounts and their access becomes a simpler task with an interface to invite, manage, revoke and report on the guest accounts. Configured with workflows, this further enables organizations to take a more pro-active approach revoking access from unused guest accounts.
How many Guest users are in your organization?
If you want to find out, you can go to the Azure Admin portal and see all Guest users. You do not need to be an admin or need any special administrative privileges for this.
1) Go to: https://portal.azure.com/#view/Microsoft_AAD_UsersAndTenants/UserManagementMenuBlade/~/AllUsers
2) Sign in with your user account for your organization
3) Click on the Add Filter button
4) Use the filter User type = Guest
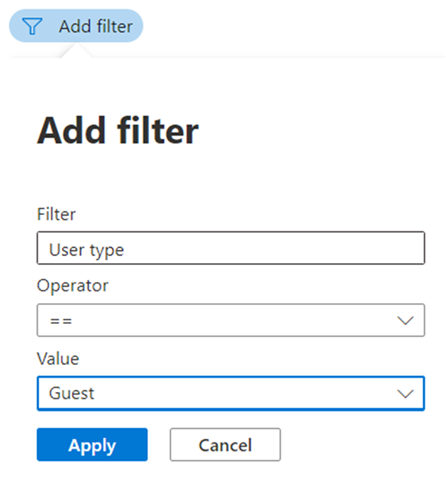
5) Click Apply to view the list of all Guest user accounts in your organization.




