So what are High Value Solutions?
One Identity have the benefit of a portfolio that embraces all aspects of the Identity & Access Management spectrum. We refer to it collectively as Unified Identity Security Platform (UIP).
Within the portfolio, there are natural solution combinations that together create a powerful offering that derive a set of High-Value Solutions (HVS).
Privileged Access Governance (PAG)
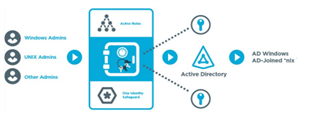
One Identity provides Privileged Access Governance (PAG) as an out of the box module in Identity Manager and then integrated with Safeguard. This high value solution integrates Identity Manager and Safeguard to provide
Privileged Access Governance (PAG) which protects and manages privileged access and grants a 360-degree view of users, accounts, and activities. The PAG integration module connects Identity Manager with Safeguard and
provides enterprise provisioning and deprovisioning, access request and approvals, delegation of roles and responsibilities, policy/SoD detection and enforcement and attestation/certification of access.
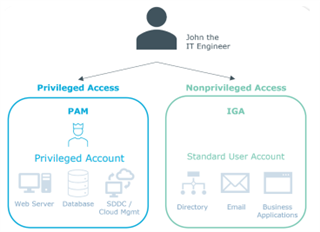
The key value of PAG and integrating PAM with IGA, is it enables organizations to leverage the capabilities (provisioning, workflows, roles, policies, risk) across to the PAM environment. PAG addresses risk and takes this
vital piece of information as part of implementing identity governance rules and determining risk across the entire organization. For instance, granting privileges to users, managing one-off privileged access needed to
complete a specific task, controlling access to privileged passwords, tracking all privileged activity for reporting.
and audits of privileged access
--> Read the PAG Solution Guide : Here
Just-In-Time Privilege (JIT)
One Identity Just-In-Time (JIT) Privilege provides privileged access to Active Directory (AD) administrators only when necessary. When the account is no-longer in use and is signed back in, JIT Privilege disables it and removes
it from all privileged groups. It then changes the password. This least-privileged approach to AD access protects accounts from compromise.
Our JIT Privilege solution combines the powerful AD Management capabilities of Active Roles with the unmatched password management capabilities of Safeguard to significantly reduce the risk of cyberattacks on
privileged accounts.
JIT Privilege reduces risk through the “rightsizing” of privileged permissions, which refers to the act of only granting privileged permissions to the resource needed, for only as long as necessary. These permissions are
dynamic and verified with each and every access attempt, with complete visibility of each user’s privileges at all times. The rightsizing and associated visibility of privileged permissions ensures your organization meets auditor
requirements for stronger compliance.
This single, automated and intuitive security management tool for AD helps companies establish sound business practices through the management of entitlements and adaptive policy enforcement tied to real business
requirements. The efficiencies gained can seriously reduce administrative burden, friction and cost.
--> Read the JIT Solution Guide : Here
Behavior Driven Governance (BDG)
One Identity provides Behavior Driven Governance (BDG) through the integration of OneLogin SSO, One Identity Manager 9.0 or later, and a Solution Accelerator, accessible via GitHub. This high value solution provides customers full visibility into whether accounts and entitlements are necessary based on how they are being used, and gives them the ability to implement policies to recommend or automatically remove unnecessary entitlements and accounts.
The solution works by having One Identity Manager evaluate OneLogin event data, including application access frequency. One Identity Manager can correlate these OneLogin applications with any associated accounts and entitlements and then, using an attestation, it provides the user's manager or responsible party the opportunity to revoke access that may not be needed due to lack of application use. Alternately, instead of providing conditional removal with an attestation, the unneeded access can automatically be revoked. Another way in which the BDG solution may be used is to ensure continuous compliance of which users are using which applications.
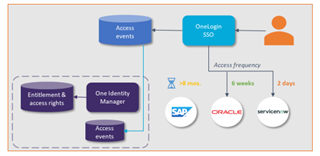
BDG enables administrators to know exactly when a user has logged into an application. That information is stored in an event log for every user, for every app in OneLogin. With OneLogin and One Identity Manager working together, this intelligence that an application has not been utilized can be used to inform the IT or compliance team that there is unnecessary access that may represent a vulnerability. It is not enough to just govern an application on the SSO launchpad. The risky part is the system account and the privileges or entitlements associated with it. The deep integration between OneLogin and One Identity Manager is the only way you can be sure that the risky access is removed in response to usage behavior intelligence.
--> Read the BDG Solution Guide : Here
Locate all the assets in Partner Circle > Here {Logon to Partner Circle required}
One Identity have worked closely with our IT department and engineered a new real-time synchronisation solutions that now uploads new and revised assets to Partner Circle on the day they are created! So the content will always be the latest and greatest, providing our partners an edge in positioning One Identity against competitive offerings.

Send us any suggestions to improve further : Engage One Identity