I have setup user access to SPS using LDAP, which works. I can sign in as an LDAP user into the SPS web portal ok
Then created a user mapping policy which maps any local user name on a test sever to an LDAP group, which my LDAP user is a member of
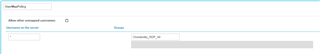
My RDP connection to the tester is using user the user mapping policy,
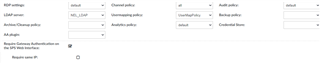
When I RDP onto the test server via the SPS web interface, my test account crednetials are recgonised, but if I sign into the SPS portal as that user, I can see the connection user gateway authentication, but no user or remote user name is shown. the RDP connection displays a blank screen.
If I remove my user mapping policy from the RDP connection I can connect onto the test server ok. What am I doing wrong? I want to use user mapping, so my test user can sign onto the server as the local administrator
thanks!