The expense to unlock a user’s account goes far beyond billable helpdesk hours but also lost the productivity of everyone impacted by the lack of user access – including the user, the user’s internal and external clients – and even the Helpdesk representative, if they have other responsibilities other than responding to user tickets.
Driving up these impacts are earnest efforts to keep our passwords safe, such as "robust" password policies. These typically involve requirements of a minimum number of characters; a combination of digits, uppercase, special characters; and other stipulations, such as not repeating any of your last 10 or so passwords. Because we are humans with busy lives and numerous unique passwords, it’s very likely that there is a proportional relationship between the robustness of policies and the volume of calls to Helpdesk to unlock accounts and reset of passwords.
I’m not claiming to uncovering new findings here, I am merely describing a situation most of us endure every day, which only worsens when organizations require more and more passwords. Nor would I be describing this problem if I did not have a solution to propose — complaining is super easy…
What do we do?
The first suggestion, backed by the ISO27001 (control objective A.11.5.3), is to implement an interactive passwords manager that ensures ‘quality’ passwords. At One Identity, we have three solutions aimed at password management:
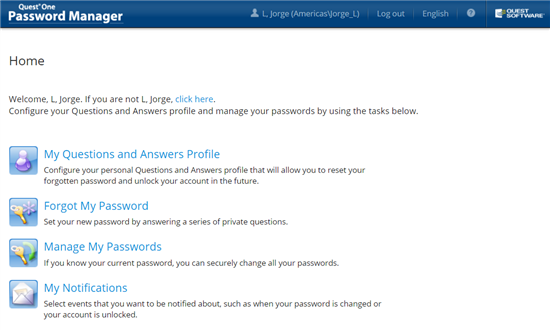
Password Manager is a web app that empowers the end user to reset his/her AD password (and connected systems such as O365 and databases, among others) and unlock his/her account without the need to call (read "wait for") Helpdesk. The solution allows for password management across multiple domains, supporting up to 16 different policies in each thus allowing you to apply those robust policies only to users whose accesses deem it necessary. With today’s social engineering questions and answers, profiles are every day more obsolete so we recommend complementing, or replacing this method of validation completely with a token or OTP.
Windows login screen integration (aka GINA) could even help to solve the problem of the initial password. Users simply access the link, the browser opens without logging into the PC, and then, after SMS or token validation, the user enrolls and sets up a password to login for the first time without the intervention of IT and without having to deliver the user that first password by any (unsafe) means.
Privileged Password Manager is our aptly named privileged password manager - and (optional module) session manager. Pre-installed on a hardened appliance, this solution automates the request, approval, and delivery of administration passwords which are critical to an organization’s operations (such as passwords used to protect firewalls, databases, the AS400, etc.). One Identity’s Privileged Session Manager tracks activities of privileged users and allows you to see and analyze what actually took place during an elevated access.
This tool can be critical to proving compliance with requirements, such as Control Objective A.11.2.2 of the ISO27001: "The allocation and use of privileges shall be restricted and controlled", and requirements 2, 7, 8, 10 and 12 of PCI DSS.
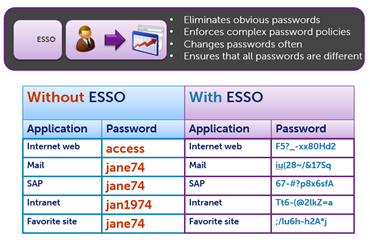
Enterprise Single Sign-on eliminates the need to remember and manually manage all the different passwords users need to access enterprise applications. These apps can be web, client-server, green screen, etc. The agent generates unique, complex passwords for each application, which avoids having the same password, or a derivative, in different systems.
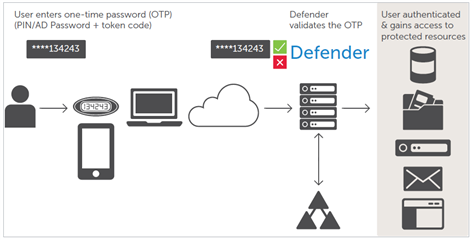
The second suggestion is to enhance security by implementing two-factor authentication (2FA). I believe this to be far more efficient than a password policy that makes them nearly impossible remember, but hardly impossible to break. This one solution could have prevented so many of the high-profile breaches we seen reported recently.
All the solutions I have mentioned here are modular and support two-factor authentication, including our own Defender, which is standards based (RADIUS, OATH) and in some cases can completely replace that darn password (!)
It is a balancing act to enhance security without compromising productivity. With the adoption of these tools, you can reduce helpdesk call volume, increase productivity, enhance security, as well as improve end-user experience. How about that? In fact, your users may start to love you more, instead of viewing you as the grumpy security person who says ‘No’ to everything. troke