Many times companies use an initial password that is partially or completely static (Summer2017?), or sometimes they use a formula which includes partial data of the user such as the month of birth + the three final digits of their Social Security, etc. We’ve all seen it…Additionally, the medium by which this initial password is delivered to the user may include sending it to their personal email or worse, printing it on a piece of paper that passes by several hands before making its way to the end user.
This POC aims to eliminate static passwords and improve the initial validation process, replacing the password with a OTP/TOTP. On this occasion we will use Active Roles to streamline the creation of a user account through a web interface, delegated to the help desk or to human resources. The tool helps us to validate and standardize the entered values, among which we will appoint the phone number as required. Once the user account is created, taking advantage Password Manager integration with the Windows login screen (GINA, SPE), the user will validate by SMS or voice call. Keep in mind that we also have the option to validate with Defender (our token/TOTP). This way the user will have Access to the workstation, email, SharePoint site, O365, databases and any other resource automatically provisioned, without the need to call the Helpdesk nor having that initial password delivered in any way. Are you visualizing the time and money savings already?
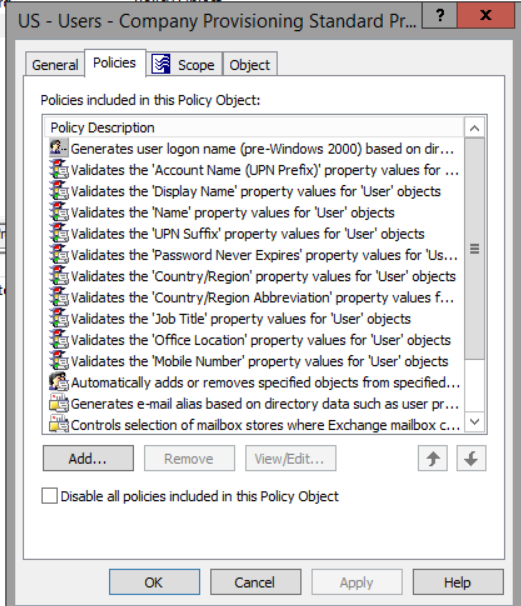
Figure 1: Provisioning policy in Active Roles.
Figure 2: Let’s create a new user account. Active Roles generates Display Name, SamAccount and other attributes automatically. 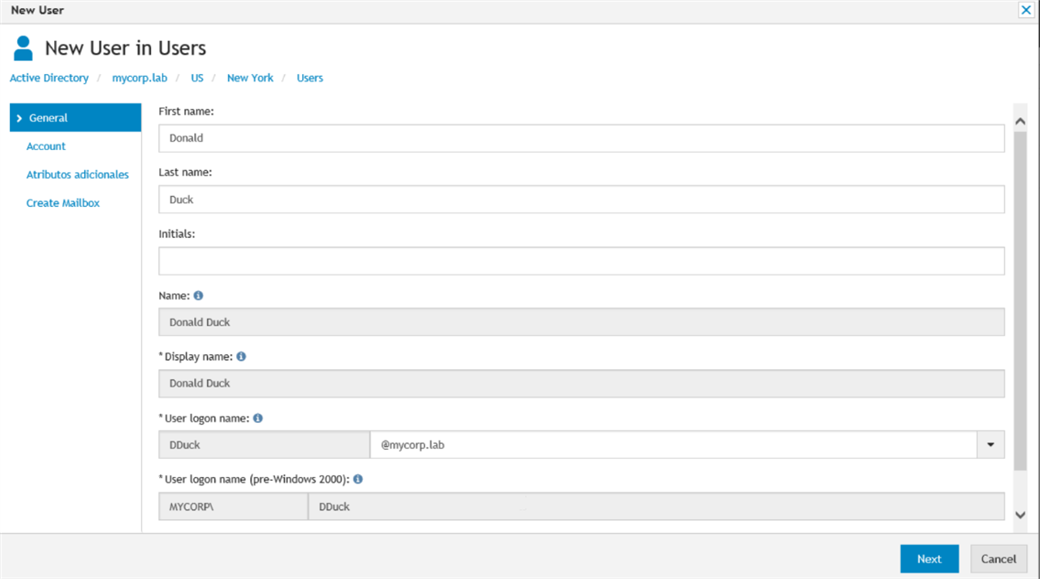
Figure 3: Active Roles can generate a unique, random password with complexity according to policy. 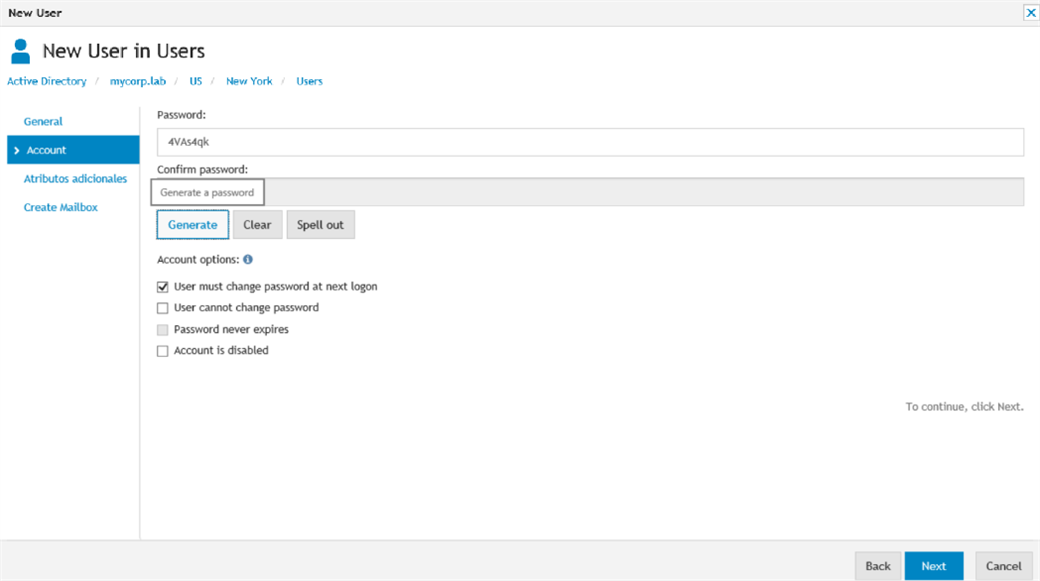
Figure 4: Fields can me mandatory, and a drop down list may be provided as well. 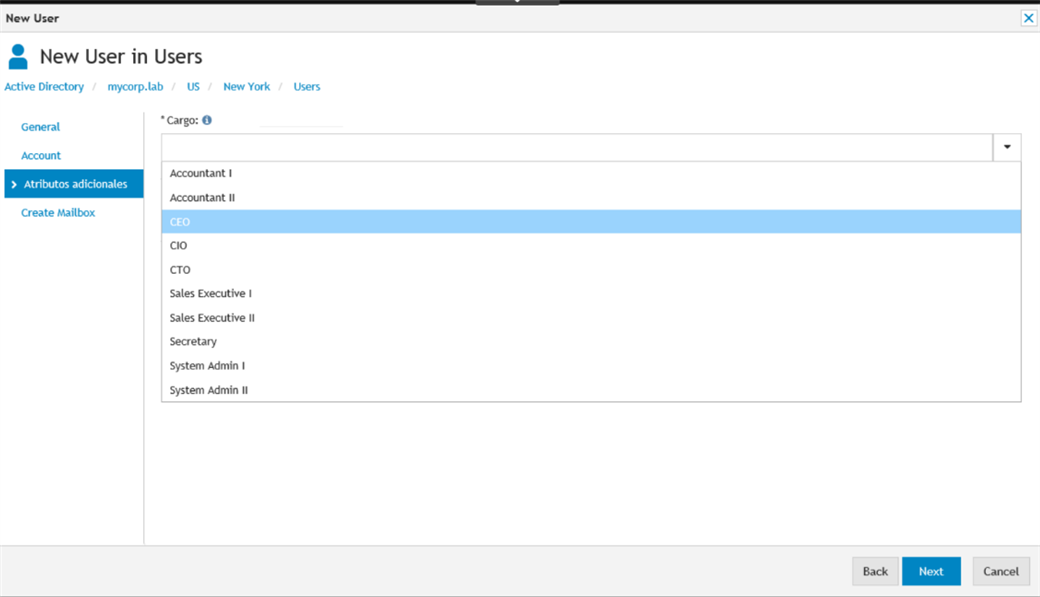
Figure 5: An Exchange mailbox will be automatically provisioned. 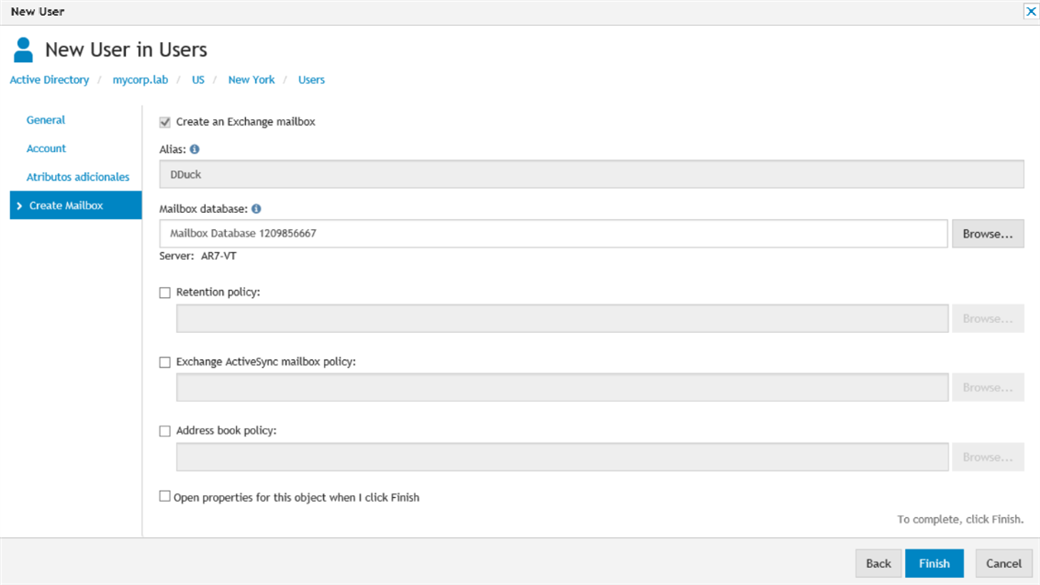
In order to avoid sending the user that initial password we will use Password Manager, particularly its GINA/SPE integration and phone validation.
Figure 6: We drag ‘n drop Authentication via phone to the workflow. As you can see on the left, Authentication with Defender (RADIUS TOTP) is also available.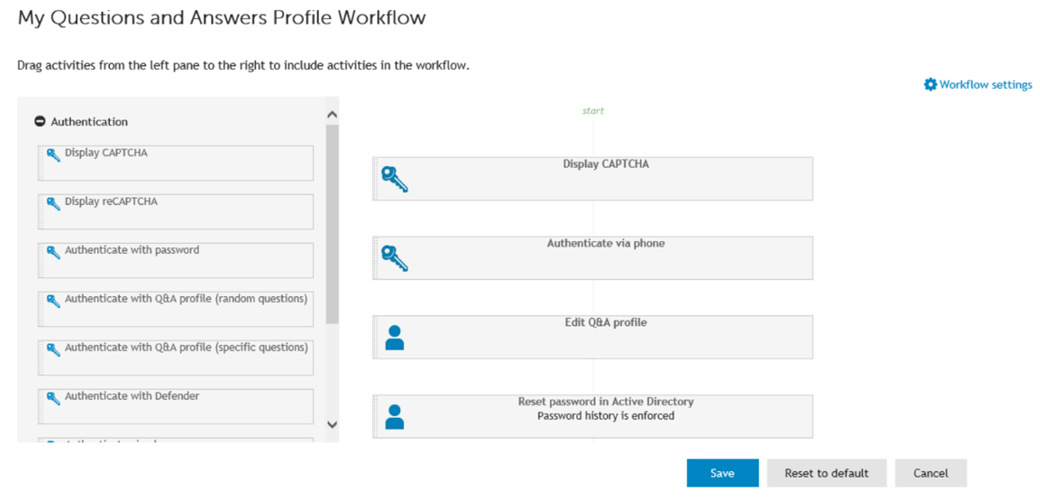
Figure 7: Configure all available options.
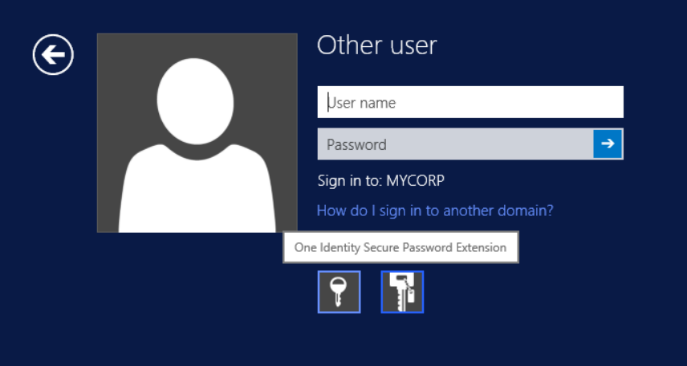
Figure 8: The user is in front of his workstation for the first time. No need to call the helpdesk, using One Identity Secure Password Extension.
Figure 9: Self-service site is accessed without logging into the workstation. 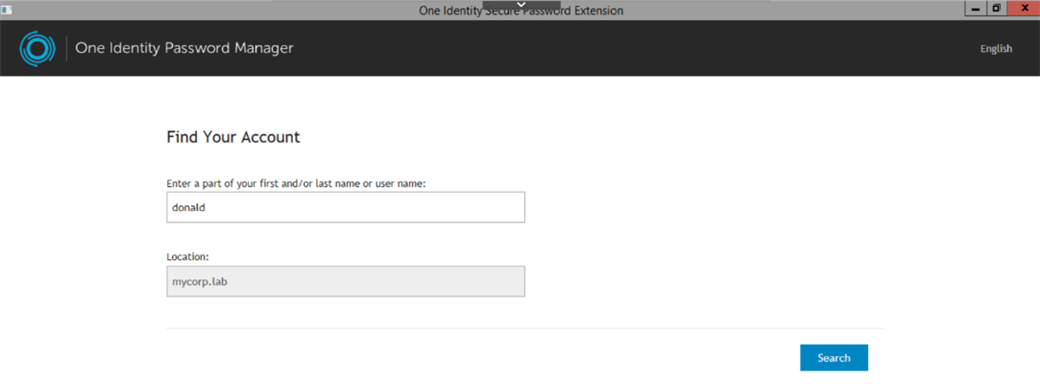
Figure 10: Q&A profile must be filled out to enroll. 
Figure 11: Captcha (configurable) to avoid automated attacks. 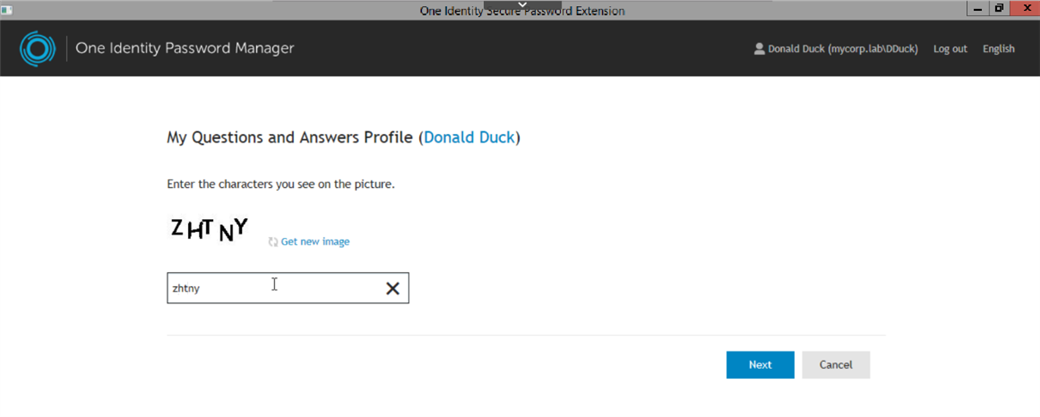
Figure 12: Password Manager will query AD for the phone number associated with the user. 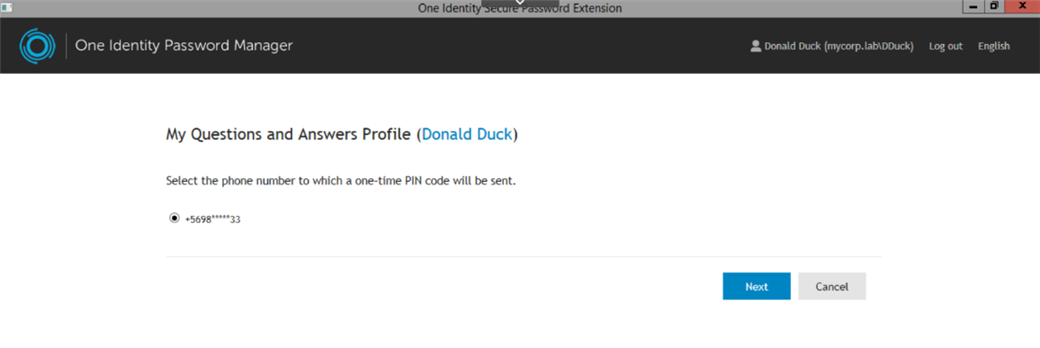
Figure 13: The user gets the SMS and enters it in the portal for validation. 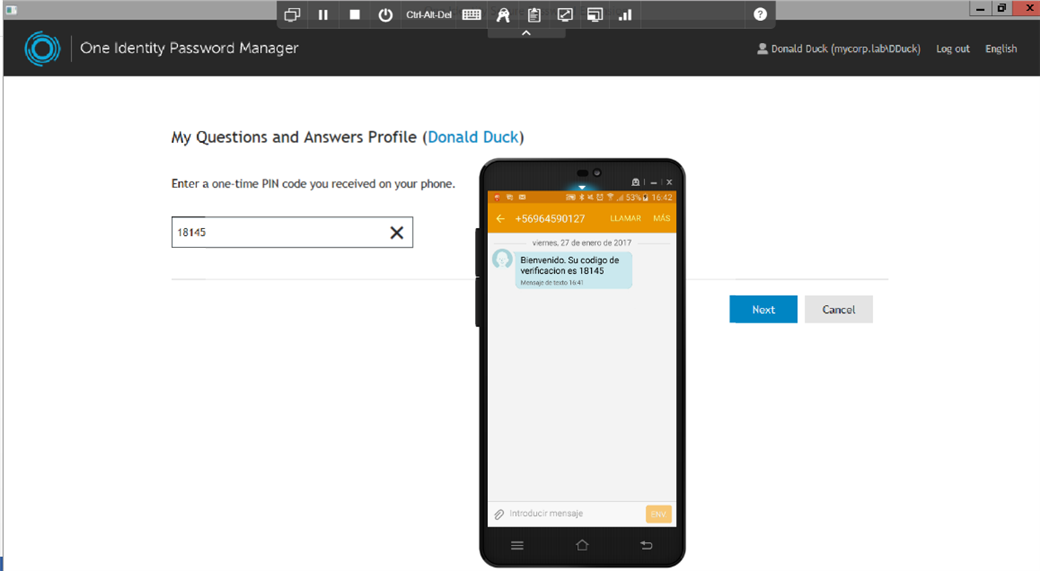
Figure 14: Q&A profile may include any combination of mandatory, optional, user defined and help desk questions. 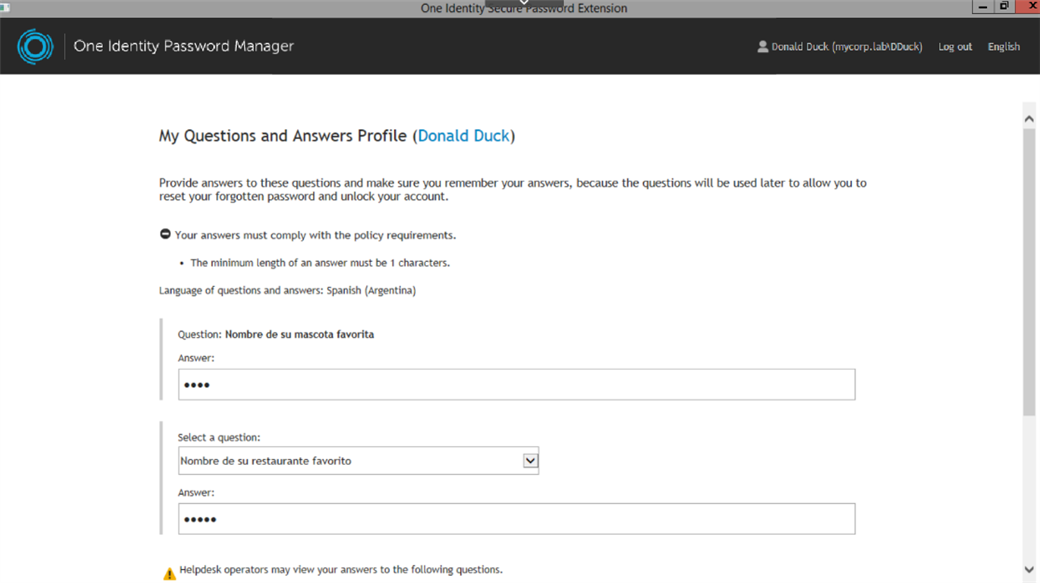
Figure 15: The user enters a new password. 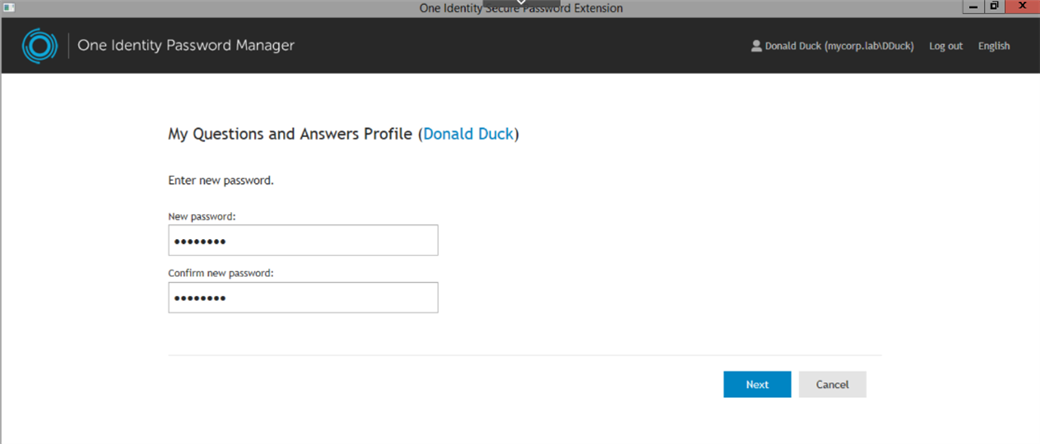
Figure 16: Success! The new user is enrolled in Password Manager and can now login using the new credentials. 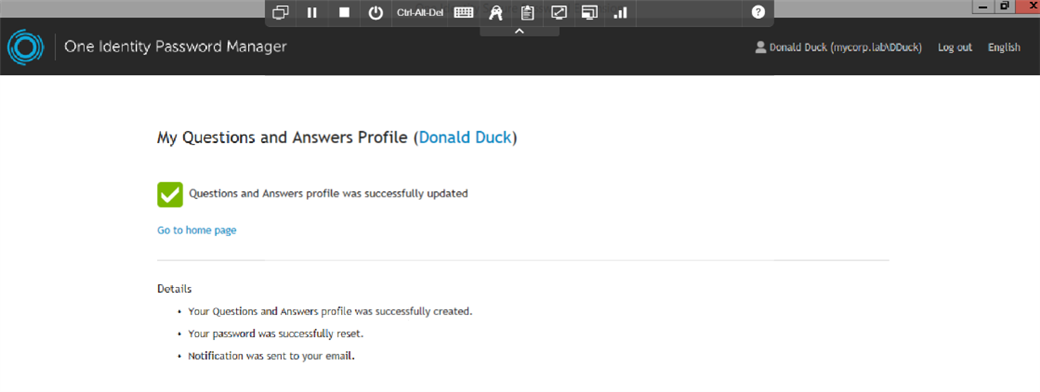
Summary
This use case involved using two One Identity tools that allowed us to solve the initial password dilemma with a unique, random and automatically generated initial password. Furthermore this password is not used as the user validates with an OTP the first time, enrolling in Password Manager in the same step. Not a complex solution whatsoever which offers a quick ROI and adds better security to the operation.
Some skeptics say that better business through better security is a fallacy… but it can be done!
Hope it helps!