We recently published a blog titled Defending Your Organization Against Session Cookie Replay Attacks. This blog thoroughly examined the menace of session cookie replay attacks, shedding light on the potential risks and consequences they pose to online security. The post delved into the intricacies of session cookie replay attacks, detailing their working mechanisms and the extensive damage they can inflict and emphasizing the imperative need to comprehend and fortify against such threats.
As a quick recap, session cookie replay attacks involve the malicious use of stored session cookies to impersonate a user on a targeted website, typically acquired through methods like malware, Man-in-the-Middle attacks or the compromise of support systems. The repercussions extend from hijacking user accounts to compromising sensitive data and even potentially taking over an entire access management system.
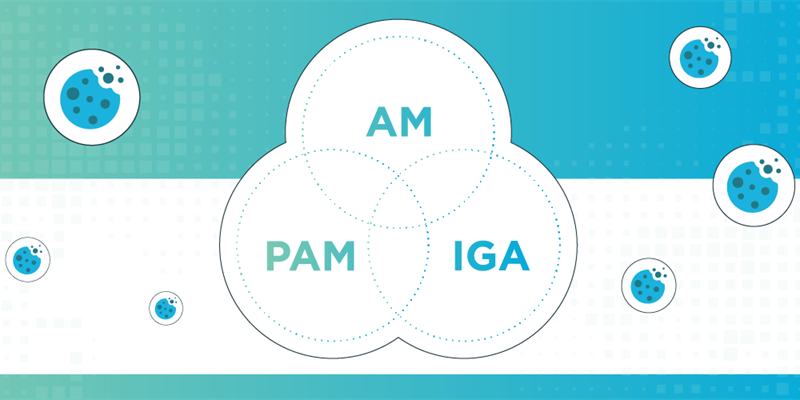
Given the continuously evolving cyber threat landscape, the urgency to establish robust defense strategies against session cookie replay attacks and other sophisticated security breaches has escalated. It is clear that fortifying cybersecurity defenses for these evolving threats cannot be accomplished fully with access management solutions alone. Organizations should adopt a multi-layered approach that also includes the advanced capabilities found in Privileged Access Management (PAM) and Identity Governance and Administration (IGA) solutions. This blog further explores this integrated approach to countering session cookie replay attacks and similar threats.
Defending against session cookie attacks by integrating access management, PAM and IGA using the Unified Identity Platform
Protecting vulnerable accounts from unauthorized access in the form of session cookie replay attacks may be best handled with a multi-layered approach including access management, Privileged Access Management (PAM), and Identity Governance and Administration (IGA) tools working together. These three layers can be summarized as follows:
Protect privileged accounts
Restrict access to sensitive or high-risk accounts, including admin accounts on your access management system, by requiring access through a Privileged Access Management (PAM) tool. Using a PAM system to control access to these accounts enables session recording and control, real-time monitoring of privileged access, password rotation and just-in-time privilege assignment.
Detect rogue actors
Control access to vaulted privileged accounts protected by the PAM solution by limiting SSO access to only authorized users in your access management system. Users must securely authenticate into the access management system to have access to the PAM tool. A user security policy for these admin and privileged users should be employed to restrict access to only trusted devices and to limit the session inactivity timeout to a small timeframe, such as five minutes. This will reduce the opportunity timeframe for attempted session cookie replay attacks to the shortest possible time.
Since access to these admin accounts are granted only through the PAM tool, the admin account should be deactivated and the session should be closed right after the administrative tasks are complete, so a short inactivity timeout would not cause undue inconvenience to the administrative users. Additionally, an application security policy should be employed to require reauthentication and MFA whenever the PAM application is launched.
Further, a module of the PAM system should apply user behavior analytics, which can distinguish the attacker from the authorized user of the account by analyzing keystrokes and mouse movement patterns. With this capability employed, the session can be terminated automatically when such an attack is detected.
Enforce and remediate
Use Role-Based Access Control (RBAC) from the Identity Governance and Administration (IGA) solution to assign access to the privileged accounts within the PAM system, and to assign access to the PAM application on the user’s access management dashboard to only authorized administrative and privileged users, creating a condition of least privilege. These RBAC policies should reduce the attack surface by revoking unneeded access for users who have been terminated or who have changed job roles, revoking PAM system’s privileged account access and assigning the PAM application in the access management tool.
Use policies to ensure the access control security policies in the access management system are correctly applied to users, admins and the PAM application. Additionally, use policies to detect rogue or orphaned accounts which may be vulnerable to attack. Employ regular access reviews in the form of attestations or certifications to ensure least privilege is maintained.
Conclusion
A successful unified approach uses the whole cybersecurity toolkit in an integrated fashion to create this multilayered approach to identity security. The One Identity Unified Identity Platform provides the necessary framework to most effectively defend against session cookie replay attacks and to ensure the organization remains protected.
Used together within the One Identity Unified Identity Platform, access management, PAM, and IGA can build a layered defense against session cookie replay attacks and other evolving cyber threats. This integrative approach enables the innovation needed to create best practices, empowering organizations to stay ahead in the face of emerging threats.
Call to Action
We urge organizations to consider the adoption of the One Identity Unified Identity Platform, including access management, PAM and IGA working together to fortify their defense mechanisms against emerging cyber threats. Embracing a comprehensive security strategy and adapting to the evolving threat landscape are critical steps toward safeguarding digital assets.