Privileged access management (PAM) is one of the fastest growing areas of cybersecurity. As virtually every high-profile breach involves compromised privileged accounts and administrative access, it’s no surprise that securing those credentials and associated access is at the top of every CISO’s priority list. Whether you’re just starting your PAM journey, filling the gaps exposed by your first foray into PAM, or optimizing your program for new target systems, I would predict that every IT leader reading this will invest in PAM technologies in the next 12-18 months in one some form.
So what is PAM?
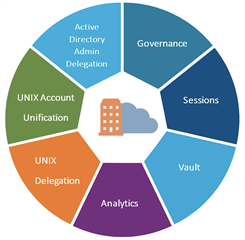 The easy answer is, “it’s a password vault”, but it is so much more. In reality, password vaulting is an incredibly important piece of any PAM program but it is not the only piece – and may not even be the most important piece. PAM is a multifaceted discipline that provides visibility into and control over activities performed with administrator credentials. This diagram shows the many areas that PAM can (and should) touch.
The easy answer is, “it’s a password vault”, but it is so much more. In reality, password vaulting is an incredibly important piece of any PAM program but it is not the only piece – and may not even be the most important piece. PAM is a multifaceted discipline that provides visibility into and control over activities performed with administrator credentials. This diagram shows the many areas that PAM can (and should) touch.
The challenge is to implement the right mix of capabilities to serve your specific needs. Does your PAM solution address all of your needs, including the ability to implement least-privileged access and Zero Trust? Do those capabilities affect your entire environment and user base, including cloud targets, DevOps, RPA users and other non-human users? Can you consume those capabilities in the way that is best for your direction and long-term strategic path – on-prem, hybrid, private cloud or SaaS?
That’s a lot to consider but the cost of not considering all of it is unacceptable. To make things a little easier, One Identity has created a comprehensive, yet easy-to-read eBook called Security Starts Here: Privileged Access Management. Download the eBook now and start your journey to PAM success.
Read Why You Should Invest in Next-Gen PAM >




Top Comments
After reading your article I was amazed. I know that you explain it very well. And I hope that other readers will also experience how I feel after reading your article. https://www.deckingbendigo.com.au…
PAM is a comprehensive discipline that offers control and visibility into actions taken when using administrator credentials. The numerous locations that PAM can (and ought to) affect are depicted in this…
-

hopecalista2000
-
Cancel
-
Up
+1
Down
-
-
Reply
-
More
-
Cancel
Comment-

hopecalista2000
-
Cancel
-
Up
+1
Down
-
-
Reply
-
More
-
Cancel
Children