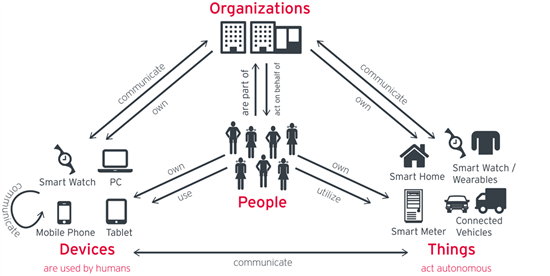
IAM programs should empower digital transformation, but organisations are at risk of being held back by mistakes from the past.
Digital transformation is rapidly taking over boardroom agendas and giving businesses the tremendous challenge of reevaluating…