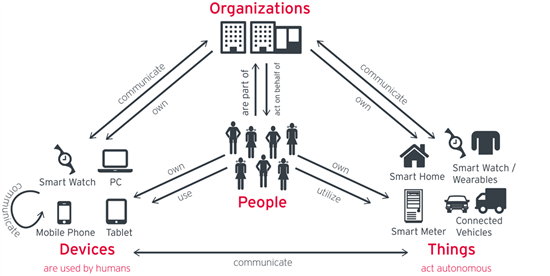
In today’s world, organizations need to have the right security policies and practices in place to prevent intrusions, protect data and ensure compliance with corporate policies and government regulations. When security enables an organization to make…