AKA: who’s snooping at your most sensitive data
Remember Gladys Kravitz from the old Bewitched TV show? Unless you are old like me, you may not. Suffice it to say she is the epitome of the nosy neighbor –always snooping into other people’s business…
AKA: who’s snooping at your most sensitive data
Remember Gladys Kravitz from the old Bewitched TV show? Unless you are old like me, you may not. Suffice it to say she is the epitome of the nosy neighbor –always snooping into other people’s business…
Here at One Identity, we like to highlight organizations that figure it out and finally get IAM right. There are so many that struggle to achieve the security, automation, and transformation that IAM can deliver, that when someone pulls it off, we like…
Striking a balance between security and business enablement is a constant challenge for any organization. Even for seemingly well-adjusted businesses, this search for the perfect world can be fraught with misunderstandings, miscommunication and political…
After the second terrorist attack in about two weeks in the UK, Prime Minister Theresa May claimed that the Internet needs regulating, and is a safe space for terrorists following on from the attack June 3rd. This got me thinking. Part of me feels this…
By Guest Blogger, Victoria Schultz, Immersion Technology Services (One Identity Partner)
Since it was established in 1889, Western Carolina University (WCU) has been bringing higher education and career opportunities to the western region of North Carolina…
I’m here at the Kuppingercole EIC17 conference and it’s Day 1. As always there’s that mix of first day of school after summer holidays and “new kids on the block” for those who attend the conference for the very first time.…

For many organizations, compliance with data security standards doesn’t seem to be getting easier. Compliance efforts often compete with projects that address information security threats and vulnerabilities, and these efforts often lose out in the battle…

While relatively a newcomer to the IT compliance scene, PCI DSS has been mandated by all members of the PCI Security Standards Council, including Visa International, MasterCard Worldwide, American Express, Discover Financial Services and JCB International…

Using the user, group and role-based management features of payment and business applications that accept cardholder data or sensitive authentication data is not enough to secure your data and ensure compliance with PCI DSS requirements.
The set of system…

Digital Transformation of business is unstoppable. It affects virtually all industries. The IoT (Internet of Things) is just a part of this transformation. Organizations that do not adapt to the transformation are risking their very survival. Furthermore…

A common misconception is that Digital Transformation is limited to certain industries, such as the ones supplying “smart homes” or “smart cities”. This is wrong. In fact, nearly every organization is impacted by Digital Transformation. Prominent examples…

Many people associate Digital Transformation with connecting things – the IoT (Internet of Things) as the quintessence of Digital Transformation. Connected things are part of the transformation, but it is about everything – business models, services…
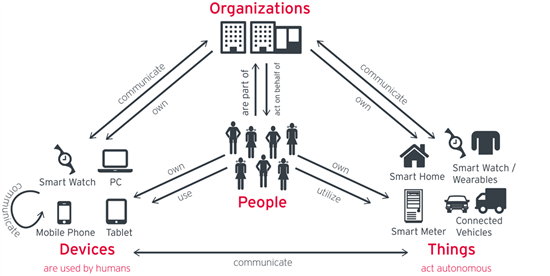
Digital Transformation adds billions of connected devices and things to what we already have in place. Therefore, we must learn to manage and thrive with the complex relationships of new organizations and their systems, devices, things and people
It…
You’ve overcome organizational and reporting challenges from PCI, SOX, HIPAA, GLB and all the other alphabet-soup regulations. Now, here comes the European Union General Data Protection Regulation (GDPR), which applies to most of us, whether we like it…