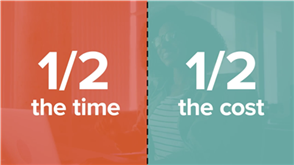
Cyber insurance has become a key component of risk management for many organizations. However, it can be difficult to keep up with cyber insurance requirements and avoid high premiums. One of the best ways to secure better cyber insurance coverage and…