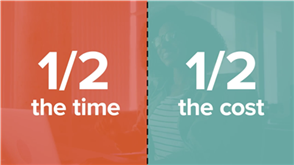
Let’s face it, AI is everywhere now. It has moved from novelty to necessity, reshaping the way we work, make decisions and secure our organizations. It guides how we plan trips, shop for essentials and discover information – but one of its most profound…