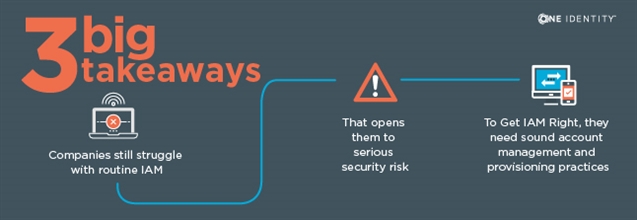
Last month, One Identity held its first One Identity UNITE conference in Newport Beach, California. Well, it was the first event that was actually branded UNITE. We’ve been having Customer Advisory Board (CAB) meetings, partner events and customer events…