Hi, my name's Todd Peterson, I'm a product marketing manager on the Identity and Access Management team at Dell Security. Today, we're going to talk about secure remote access, and how it's a tough balancing act to get it right with all the different factors that are involved. So let's start out looking at the difference between security and users.
So when you think about security, what does security need? They want minimal risk, they want maximum control, and they want accountability for all users. That's kind of counter to what the users want. Users want to be able to get to the stuff they need to do their jobs from anywhere, in any way they choose, at any time. In other words, they want maximum convenience.
So, it's not the same. You can't have security and happy users, at least normally. So something's got to give. So, you usually have a compromise. You do something for each of them.
And what do you end up with? Security ends up with disgruntled users. They've put barriers in the way of users getting to the things they need to do their jobs, they're not happy, security hears it, and no one's happy. You've got out-of-band requests.
If somebody all of a sudden needs access in a way that's different from they normally access things, somebody has to jump in and create that access for them. It slows things down, makes everybody unhappy there. And they've got more stuff to manage, we'll talk about that in a second.
But what do the users get? So they end up getting more hoops to jump through. They've got more passwords to log onto, more processes they have to go to get to certain data sources from their phone, as opposed to their laptop, or as opposed to on-prem. You've got lots of no from IT, or maybe lots of yes, but. And the but is a lot of things that they have to do in order to achieve the yes.
And normally they're compelled, or at least feel compelled, to find ways around security. You think about the person but it's difficult to remotely access certain data sources. They may download those, upload those onto Box, go home, download them from box, work on them, put them back in Box, go back to the office the next day, download them, and update the original data source. That's obviously a violation of security.
So there's a number of ways that you can grant people secure remote access that are secure. We'll talk about two of them today that, when coupled together, make a great end-to-end solution. The first is the SSL VPN. The way an SSL VPN works is it's a direct pipe from the remote user, through the firewall, to the network.
The access control is the same as the access control that exists on the network. And the way it works is you have a client on the person's computer that allows them to access that, that gives them another login that they need in order to get to things. I've worked at a company where I actually had to go through two separate VPNs to get to certain sources. And my delay from starting to log in to actually getting the stuff could have been 10 minutes sometimes, which wasn't very happy.
The pros of an SSL VPN are the access is fully in control of the organization. And it's a direct pipe into the network, meaning you know they're getting to the stuff, and you have control over who they are. You put the client on their machine, and all those types of things.
The cons are, it requires a client. It only works with machines that you control. It's a heavier management burden, meaning there's another piece of infrastructure that has to be managed, another thing that could break, that people need help with. It lacks flexibility, it's kind of an all or nothing. The same access rights you have on-prem are the same ones you have remotely, because that's just the nature of it.
Another hoop for users to jump through, as we talked about, another password, another thing they need to do. And it may not be appropriate for partner connectivity. Do you really want to give your partners or whomever a direct pipe into your network to give them access to certain subsets of the data? So that's something to consider if you have a VPN.
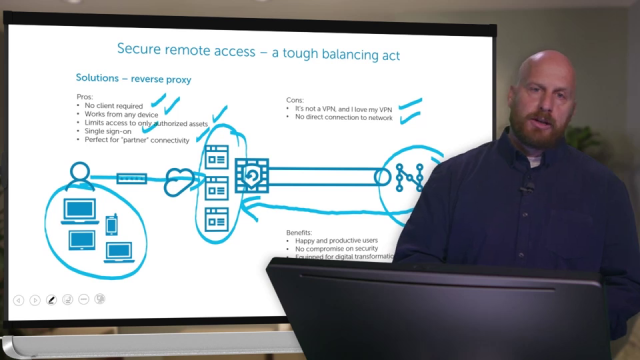
Let's turn to the next option, which is called a reverse proxy. The way it works is, you present outside of the firewall, in what's called the demilitarized zone, those applications that are approved according to the person's role, for them to access. So it may be on-prem, they have read and write rights. But when they're remote they only have read. It's possible, that-- The network stays the same. The user then accesses through the cloud, this demilitarized zone. That means they can use any device they want, because there's no client required. They can use the company-issued device, the same when it does the VPN. They could use their own laptop. They could use a phone, they could use a tablet, they could use a shared computer. Whatever.
So the advantages of the reverse proxy is there's no client required, as I just mentioned. And whatever device you choose will work. It limits access only to authorized assets, meaning the only things that are presented to the user outside of the firewall are the things you want the user to see.
It also, then, just a natural byproduct, is you get single sign-on. If each of these applications has their own login requirement, the fact that you're going through a reverse proxy means that you log into the reverse proxy, and are automatically authenticated to these applications. So you get a web single sign-on scenario, which is a very big convenience boost for users. And it's perfect for partner
 07:08
07:08
