Here's a short demo of some of the Safeguard Remote Access capabilities.
I'm already logged in to the service, remote-access.cloud.oneidentidy.com/connections, and we'll see here that we have the connection points, or cards, if you will, that present to the users. These are the published access points.
We have two categories, one for R-D-P and one for S-S-H. You do have options to filter down on protocols, by policies, et cetera. In this example, I'm going to select this mem5.iam.corp server, and log in as the domain administrator account.
This is assuming that I've already checked out the admin account from Vaulting Technology, such as Safeguard and privilege passwords. I'm going to click connect, and momentarily we'll be connected via the Safeguard session appliance, and be prompted for the authentication.
Here we go. Supply the password, and we'll be logged in here momentarily. Again, this is just using the end-users browser of choice. We're logged in.
Another example would be the S-S-H connection types. Down below, I'm going to select the centos 7-1-3-8 server, and login is route. Assuming I know what the password is, I'll click connect and be prompted for the password here momentarily. Supply the password, run a few commands, and we're logged in.
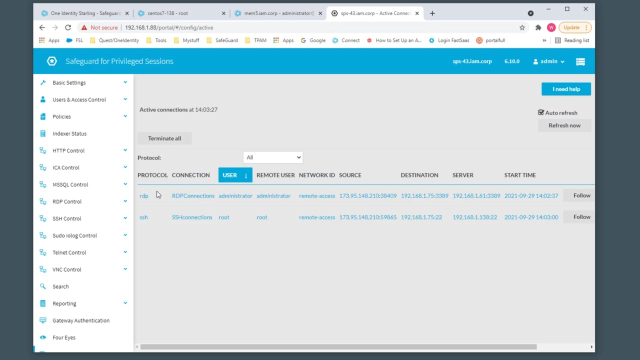
If I jump into the actual Safeguard appliance itself-- quick little refresh-- we're going to see the two connection types. On the left-hand side, we've selected active connections. This is showing me the two connections that have just been established, one for R-D-P, and one for S-S-H. Again, you'll see the remote users logged in as administrator and root, coming in from remote access, or starting platform, source I-P destination, server side, and again, you do have the option to follow or terminate the connections if necessary.
If I go to the search menu option, we're going to see some of the active connections. I can also drill down to each one of these connection points. It just gives us a high-level configuration of the I-P address, time, et cetera. Some of the analytic scores, behind the scenes, whether the log in was unusual or not.
We can go to details and it shows a little more granular information about the actual connection down to the channels-- whether we're accepting or denying, et cetera. Timelines, again right now we're still active. So what we could do is terminate the session, and I'll come back over here and I'll do a quick little exit. Wait a few seconds, and we'll do a little refresh, and you'll see now the commands were just executed inside that session itself.
So you have the who am I, the L, my typo, L-L, and exit. You can select each one of these timelines that'll show a screenshot on the right-hand side of the actual command itself.
You can also look at the analytics of the session. We give you a summary that highlights some of the patterns, and whether they fit the normal behavior for the user or not. We can see the frequent item set, that gives us multiple points as to the connection, time of day, the length of the session, the protocol being used for that user, and whether it fits within his or her normal patterns.
Host log in, some of the commands are executed. Again, we can see my little typo L, that it's unusual. Some of the normal ones, are the login time and keystrokes. Being that I wasn't in there very long, there was no baseline actually found.
You do have the option to replay the videos. So I'll click play video. We can see the commands being executed during that session.
And that concludes the demonstration of Safeguard Remote Access.
 04:53
04:53
