Hello and welcome to the technical deep dive session [INAUDIBLE] on Identity Manager with SAP. My name is Cengiz Tuztas. I'm a presales architect at One Identity, and I will introduce you to the SAP ecosystem, the basic SAP R/3 principles, and the SAP cloud platform, and how we integrate with these systems using One Identity Manager.
I will provide a deep dive into a support on on-premises AP modules like HR, org management, SAP user and role management, SAP authorization model, and segregation of duties, capabilities, and evaluating the SAP authorization model to achieve the SAP functionality. I will discuss the SAP cloud ecosystem and talk about SAP Cloud Platform and SAP cloud offerings, like SuccessFactors and SAP Concur.
Before we begin with One Identity Manager's capabilities around SAP, we need to have a common understanding about what we are talking. The SAP ecosystem is very rich, and we have to understand what the customer actually means when he talks about SAP. So let's start with a brief introduction to the SAP ecosystem.
The SAP ecosystem consists of a variety of on premise and cloud offerings around core business needs. The main service provided by SAP is the SAP Business Suite. The SAP Business Suite is a bundle of business applications that provide integration of information and processes, collaboration, industry-specific functionality, and scalability. SAP Business Suite is based on a SAP's technology platform called NetWeaver. The SAP Business Suite contains SAP ERP, the Enterprise Resource Planning solution, SAP CRM, Customer Relationship Management solution, SAP SRM, the Supplier Relationship Management module, SCM, Supply Chain Management, and PLM, or Product Lifecycle Management.
The SAP S/4HANA, high performance analytic appliance, is the successor of SAP R3 and SAP ERP and is optimized for SAP's in-memory database, SAP HANA. SAP S/4HANA is provided in various offerings. I will get back to this later. And the SAP Cloud Platform is an enterprise platform as a service that provides comprehensive application development services and capabilities, which lets the customers build, extend, and integrate business applications in the cloud. SAP also provides software as a service offerings like SAP SuccessFactors, Concur, Ariba, Hybris-- these solutions have been acquired and provide cloud HR and travel and expense management services in the case of SuccessFactors and Concur.
When we talk about the cloud platform and the applications that are available on the cloud platform, we always encounter Cloud Foundry and Neo. To have an understanding of what Cloud Foundry and Neo is, the Cloud Foundry is an application runtime which is based on open source. Application developers can use the Cloud Foundry environment to enhance SAP products and to integrate business applications as well as to develop entirely new enterprise applications based on the business APIs that are hosted on SAP Cloud Platform.
The Cloud Foundry environment allows customers to use multiple programming languages such as Java, No.JS, and community languages, whereas the new environment contains an SAP propriety runtime. It is a feature-rich and easy-to-use development environment, but only allowing to develop in Java, SAP HANA XS, and HTML5. Customers can also use SAPUI5 to develop rich user interfaces for modern web-based applications. The new environment also lets customers use virtual machines, allowing them to install and maintain their own applications in scenarios that are not covered by the platform. Cloud Foundry and Cloud Neo applications are running on the SAP Cloud Platform and can be maintained using the SAP Cloud platform connector of One Identity Manager.
When we talk about SAP R/3, in most cases, SAP means for customers, their on-premise SAP business suite components, primarily, their ERP system, which is R/3 or ECC, and more and more S/4HANA now, but also components like CRM, Customer Relationship Management, and PLM, Product Lifecycle Management systems, are available. On One Identity manager's site, the connector provides connectivity to the HCM, BI, R/3, ECC, or S/4HANA on-premise edition.
For S/4HANA, One Identity Manager provides connectivity premise edition only. For the different deployment options that are available, like the cloud deployment options, are available as a cloud private option and the cloud public option. The cloud private option is the SAP S/4HANA Cloud Enterprise Edition Private Option. The Cloud Public options contain the Cloud Enterprise edition, Cloud Professional Services edition, and the Cloud Marketing edition.
One Identity Manager's connector supports only the S/4HANA on-premise edition. A connection to the cloud private option might be possible if the require transport packages for the connector can be deployed on the Cloud Private option. The Cloud Public options are not supported by One Identity Manager's connector, since these services do not allow the installation of the required transport packages or provide the necessary connectivity or access. However, these systems can be connected using other options, like SCIM and RESTful APIs.
SAP HANA, SAP's in-memory relational database management system, is confusingly, very similar to SAP HANA-- SAP S/4HANA. And this often causes confusion about what component it is that is being currently discussed. Sometimes, SAP HANA and SAP HANA are being confused, because SAP HANA is being used for the database as well as for the S/4HANA system. It is very important to understand what we are talking about, because the SAP HANA database is not connected using the SAP connector. The SAP HANA database is connected using One Identity Manager's ADO.NET database connector. The SAP HANA database connector provides a specific schema retrieval, implementation, and requires the ADO.NET data provider from SAP. Customers should have access to it and should be able to provide it. Due to licensing implications, it cannot be made available by One Identity Manager.
One Identity Manager SAP connector-- which is the only a SAP-certified connector, by the way-- and the ADO.NET database connector provide connectivity to the on-premise world of SAP. For the cloud world, One Identity Manager provides three connectors via our One Identity Starling Connect service. One Identity Starling connect is a software as a service offering that provides connectivity to cloud applications by exposing a SCIM interface to be consumed by One Identity Manager or other solutions and handles the connectivity and management to cloud applications.
It acts like a proxy and translates native API access to SCIM. Starling Connect also follows the configuration for this idea of One Identity Manager, setting up connections, exposing endpoints, and mapping native attributes for cloud applications into the SCIM namespace and hereby providing to the consuming applications like One Identity Manager, are being completely configuration driven. No coding or scripting is required.
One Identity Starling Connect is offering a constantly growing support for a wide range of cloud applications, not only limited to the SAP cloud ecosystem. For the SAP Cloud system, Starling Connect is providing the following connectors, the SAP Cloud Platform, Success Factors, and SAP Concur.
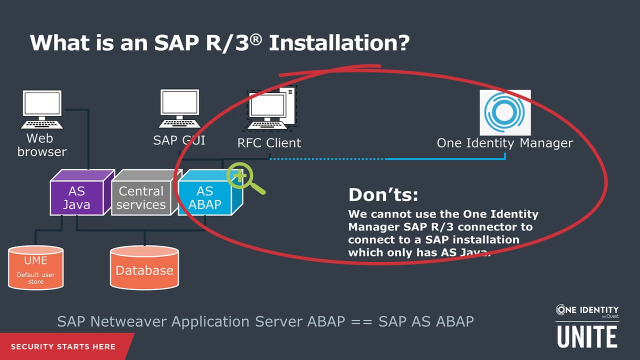
Let's look deeper into an on-premise installation when we talk about an SAP R/3 installation. And this SAP R/3 installation consists of a database. Database can be, depending on which system you use, either S/4HANA or any available database system. On top of the database, the central services resides. The central services are being used together from two different application server flavors. One flavor is the application server Java, which is a Java application server which uses central services and has access to the database and provides applications that can be accessed using the web browser by business users.
The second application server option is the ABAP-based application server. The ABAP-based application server is the more common application server and the widespread application server. The access to ABAP system is mainly done using the SAP GUI, which is the prominent application to access, or the well-known application to access an SAP system. However, it also provides the RFC access. And this is the access that One Identity Manager also uses to access the system. So One Identity Manager connects to the application server [? RBAP ?] using an RFC connection and operates on the database data provided in the system. So whenever we talk about an SAP NetWeaver application server, it is the application server ABAP.
For the Java system, we also have UME. UME is the default user group role store for the Java application server. The UME can also consume NetWeaver ABAP as a user store or can consume other systems. When we look in more detail into the SAP UME adds business value by enabling customers to leverage their existing infrastructure by accessing user-rated data on an existing LDAP Directory, an SAP NetWeaver application serve for RBAP system, or a database.
The UME runs as a service in SAP NetWeaver application server and is the default user store for this. The UME can be configured to read and write user-related data from and to multiple data sources. So applications or users in the system can come from different user stores in the backend. UME supports access using the Service Provisioning Markup Language, SPML. And using SPML accessing the UME is the recommended way of accessing the UME or managing users and roles in as SAP UME. As you might see, we have access or connectivity to the LDAP directories or ABAP systems or databases. However, we would recommend using the UME to fully leverage the capabilities of SAP UME to manage users and roles.
What is an SAP R/3 installation? We have seen a more global view previously, and in detail, when we look at the different layers, at the bottom, we have the database management or database layer, as mentioned. Depending on which version of SAP is being used, this can be the usual suspects up to ECC. It can be an Oracle database, a Microsoft SQL server data, is PostgreS, [? Autobus, ?] MaxDB. Starting with S/4HANA, the underlying database must be SAP HANA.
The application layer can either be ABAP or Java. And on these application layers, there are the different SAP applications that use the kernel or central services. And these applications are also called modules. Some modules are, for example, the finance module, controlling module, or production planning, or even the Human Capital Management or the HR module. The HR module is an application on the application server, on the SAP system, or the finance module is the application on the system that provides financing or financial accounting functionality to the enterprise.
The presentation layer provides access to apps or users. Proprietary access is being performed SAP GUI or standard web pages. And modern installations use the SAP Fiori applications. With the SAP Fiori, some confusion might be possible here as well. SAP Fiori is SAP's modern HTML5-based UI. These are called Fiori apps. These Fiori apps are not to be confused with the applications or modules described here. The SAP Fiori applications are more like classic transactions in an SAP system.
How does the communication with the SAP system actually work from One Identify Manager's perspective? One Identity Manager uses an RFC connection to access the system. Through the RFC system connection, business functions can be executed. These business functions are combined to so-called packages, like user, as you can see here, or others, as well. One example for such a function is the RFC_READ_TABLE function. This function will require some parameters and will provide the functionality to read the table.
Roughly speaking, the RFC_READ_TABLE function is [INAUDIBLE] around SQL SELECT_FROM_TABLE state. Not all functions are just like this. RP functions can contain very sophisticated business functionality and logic to retrieve and evaluate existing data across several tables.
To be able to access the RFC layer, we need the SAP .NET Connector 3.0. What is the SAP .NET Connector 3.0? The SAP NCO is the middleware to call RFC functions on an SAP system. It needs to be downloaded separately from SAP and provided by the customer due to licensing implications. One Identity Manager requires version 3 for the .NET 4.0 or higher in the x64 version. The SAP NCO files need to be installed either on every system that needs to talk to the SAP system, like job servers and admin workstations, or better, should be uploaded into One Identity Manager's database via the software loader tool. If there are any issues with the connectivity, the RFC trace environment variable can be set to 1 and will provide a trace log of the communication with the SAP system.
In addition to the SAP NCO, the SAP client that needs to be managed via One Identity Manager needs to be prepared. For this purpose, One Identity provides a transport package for SAP which contains the One Identity Manager BAPI functions. As explained previously, BAPI functions are used to execute programs on the SAP system. One Identity Manager provides the package with the namespace VIAENET containing functions needed for the SAP connector to perform the deep and comprehensive integration with the SAP system. These transport packages are part of our SAP connector, and as such, certified by SAP. These transfer packages are needed to connect One IM with SAP and must be deployed or enabled for each client that needs to be managed by One Identity Manager.
Very often, we get the question whether this transport packages can be removed again. Yes, these options are possible. So for test systems, when we deploy the transport packages and after the test, transport package can be removed from that system.
Sometimes when we talk to our customers, they already have a long history with SAP and have encountered identity or account lifecycle challenges for a long time. SAP's answer to this was the Central User Administration, or CUA, in the beginning, before IM systems were available. The CUA is a master system that is being used to centrally manage users on different clients on the same or different SAP systems. When the CUA is enabled, user administration on the child system or client is locked. Access to these child systems is being assigned through the central system. Permission management is also being performed by the central system. So role assignment will be done via the central system.
One Identity Manager's connector is fully aware of SAP's CUA infrastructure and provides dedicated support for such a landscape. One Identity Manager can use the CUA to perform account lifecycle management tasks, if the customer wants to keep CUA infrastructure, or can take over the CUA's tasks by fully implementing the account lifecycle management in One Identity Manager. Even a mixed operation is possible, where some systems are being connected via SAP's CUA, and other is connected directly, giving the option of a soft transition from CUA to One Identity Manager. For setting up an SAP R/3 synchronization, please also review the documentation for users and permissions, installing the One Identity Manager BAPI interface, creating a synchronization project, and special features of synchronizing with CUA's systems.
One Identity Manager supports various architectural setups for existing SAP systems. Depending on the customer environment, we might set up a direct communication with the R3 system application server to access the SAP client. This is a very common scenario and is a direct link between our job server and the SAP system. This option is very widespread and very common for small and midsize deployments. We also see them in larger environments.
But for larger environments, a more common scenario is the scenario described in this slide, describing the communication through a message server. This setup is, as already discussed, very common in very large environments where the messaging is kind of a load balance. Several application servers are grouped together behind the messaging server, and upon log-on, a specific application server will be assigned for this connection. This application server will then service the subsequent requests. No specific application server information needs to be provided during the configuration. This will also be handled via the underlying SAP libraries that are being used by One Identity Manager's SAP connector.
The third option is a communication through SAP Router. This is very common scenario in the SAP environment of a customer being hosted by a third party. In this case, an SAP R/3 Router host is available in the local intranet, and this system acts as a router to the customer's SAP environment managed by a third party. Subrouter configurations can be very tricky and complex. One Identity Manager, using the SAP NCO libraries and the standard SAP protocols, can handle all these setups with multiple router chains might exist in the customer environment.
 22:01
22:01
