[MUSIC PLAYING] Hello, and welcome again to Berlin office. We are talking about One Identity products. Today, we are talking about One Identity Manager. And together with me in Berlin office, there is Ingvar Johansson. He is a pre-sales engineer and expert for One Identity Manager, and he will show us what One Identity Manager maybe can do for you. Ingvar, what we will see in that video series?
The video series is divided into two sections. First, there is an overview. And the overview will cover things like what's included, what will you get out of this solution, the One Identity Manager? And secondly, we do have demo scenarios. Demo scenarios will show you things like join and move labor processes, it will show you access re-certification processes, it will show you how you request things and what the approval looks like. And also governance functionality, such as compliance rules and segregation of duty rules.
Great. That sounds really of interest to me, maybe to you as well. And now let's start with that demo.
In the classic world of user administration, you typically can find two scenarios. One scenario, the one on the left side, is what we call target system centric administration, that means there is one big target system, the important one, very often, Active Directory. And this target system gathers from some other sources lists or other systems, like an HR system, a little bit of information so that users can be created. This specific target system is then used to autentify the users and sometimes as well to manage a little bit other connected target systems depending on connector software you have installed in these systems.
Very typically for this is that for that main target system exists as well a target system admin like for the other systems. And these admins are the technical experts who do the domain management which is necessary. Additionally to that exists in companies as well the business administrators. These are people from the business without a technical background. And they do have dedicated permissions just to do something in the main target system. This is, again, what we name the target system centric administration.
And opposite to that exists, on the other hand side, this time, the right side, the classic identity management approach. In this specific approach, we have one system more-- the identity management system. And we have a clear structure. First of all exists something we can named the authoritative sources. Authoritative sources could be an HR system, an organizational management system, and so on. And they deliver data which is authoritative for the identity management system.
Connected to the identity management system exists target systems. And it makes no difference which target system at the end it is. All of them have users and permissions and they get controlled by that identity management system. It exists as well the group of target system administrators like before, and they do have the same permissions than before in the other world on the target system side.
Completely different is the approach from the business managers. These business people do not have any access to target systems anymore. They now have access to an identity management solution and they do with their business administration there. From provisioning perspective, the identity management system will then use a connector, that means a system-based agent just to provision something in target systems, which at the end limits the amount of permitted users to an absolute minimum.
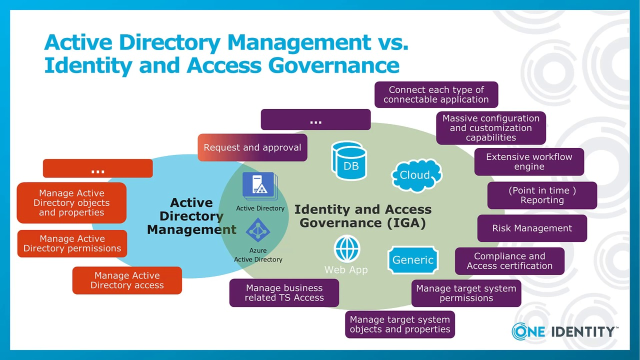
After we identified differences between the structural approach and the management approach, it is time to drill one step deeper into these solutions and figure out what is the difference between an Active Directory Management solution and an identity and access governance solution. First of all, the size is different. The Active Directory Management solution takes typically care on Active Directory and Azure Active Directory and depends on the solution a little bit on the connected target systems. But each of these connections are typically connections with a small bandwidth.
The Active Directory Management solution takes care on all Active Directory objects and it manages typically, as well, the access to the Active Directory former admin perspective. In difference to that, the identity and access governance solution [? doesn't ?] really care on Active Directory specifics. This solution typically is to manage a target system from a user and permissions. That means entitlement perspective. And this will happen to all connected target systems. And the connection to other target systems is something which is just a base feature of an identity and access governance solution.
Further, such a solution typically comes with a featured web portal where business, that means standard users, can request and approve their entitlements they need to do their work. The whole thing is just developed to be used from business people especially because nobody expects that business people know something about a platform landscape, which just provides all of these entitlements we talked about.
And then, the complete governance part of the identity and access governance solution differs from an Active Directory Management systems. Things like compliance rules or, for example, attestation which means the review of given permissions in the same way than the management of identity and access governance solution permissions as well, massive configuration customization capabilities to allow to adopt all processes a company might have, extensive workflows to support that, and risk management typically completes the feature set of an identity and access governance solution.
Last but not least, [INAUDIBLE] reporting, which is one of the main important features each identity and access governance solution should have. The whole thing, again, is built for the business, it is built for auditing, and it is built to support business needs.
If you are to stand in front of that decision to figure out if an Active Directory Management is something you need or an identity and access governance solution, the question could be easily answered. If you have to manage mainly an Active Directory or an Azure Active Directory and you are typically interested in joiner mover leaver processes, the Active Directory Management solution is what you are looking for. If you are interested to connect hundreds or only heterogen networks with different systems and applications.
And if you are interested in rich compliance features like you need for risk management or compliance, then it is necessary to look at an identity and access governance solution. Joinver mover leaver processes, as we have learned, exist in both systems, and of course in the solution world of One Identity exists as well as some requests and approval processes in both systems.
However, we talked about Active Directory Management and identity and access governance. And in the world of One Identity, we talked also about active roles on the left-hand side and Identity Manager on the right hand side of the slide.
[MUSIC PLAYING]
 08:13
08:13
