We are now going to take a closer look at the Privileged Access Governance. My name is Ingvar Johansson. I work as a Presale Engineer at One Identity in Sweden.
The Privileged Access Governance, or the PAG, is a module in Identity Manager. This module allows you to connect and integrate your Safeguard appliance into Identity Manager.
In the video series, we're going to take a look at the integration from an overview perspective. We're going to talk a bit about the connector configuration. We're going to talk about the management capabilities you have on the PAM user and the PAM group objects in Safeguard.
And, of course, we're going to cover the governance part. And the typical governance part is, of course, the ability to do access reviews. And we're going to look at how deep those reviews actually goes with this integration.
And finally, we're going to look at some extensions you get in this module where you can actually use the IT-shop to request a password release or a session.
To get an overview of the integration, we're going to start the Manager tool in my little demo lab here. Now, I've already connected to Safeguard appliance in my demo lab. And I have synchronized that Safeguard appliance into the Identity Manager.
Once you have installed the PAG module, you will have a menu option here on the left hand side called Privileged Account Management. And if you look at the options you have here, you can see that you could have one or multiple appliances synchronized into the system.
I only have one appliance. So I click on that one, and I get an overview. OK. What we see on the screen, the things you see up here and the things you see here, is really information from Identity Manager. But this is information coming from the synchronization itself.
I can see I've synchronized the virtual appliance. It's called Safeguard SPP. I can see it I have 19 PAM user accounts and five PAM user groups.
I can also see the assets. That is really the system that are being controlled by this PAM appliance. And I can see some asset accounts. I have a very limited number here just, not to confuse, to make it very simple.
We can also see the PAM entitlements. Entitlements is really something inside the PAM appliance itself. And if I click on one of the entitlements, for instance, this password, I can drill down into that one. And I can actually see what request policy that applies to this particular entitlement. So we do have every object, almost, synchronized into the Identity Manager.
If I go back again from this screen, I can also take a quick look at, for instance, one of the PAM user accounts. And I'm going to select Julia here. There's a user account called Julia B or Julia Becker's account. If I click on that, I can see that this account belongs to the employee Julia Becker.
So if I click on Julia Becker, obviously I will have the view on the employee inside Identity Manager now. She has an Active Directory account and one Active Directory domain here. She has an account in a sales report system. But you also have this PAM user account.
So going back to that account again, as you can see, she is also a member of one of the PAM user groups. If I click on that group, I can say, OK, what about this group? Well, she's not the only one, of course, who is a member of that group. But in this group, you have one of the PAM entitlements.
So obviously, if you are a member of this PAM user group, you are probably able to request passwords inside the PAM appliance itself. I have also published this particular PAM user group as requestable in the IT-shop, which essentially means that any user is a PAM user who are allowed to request this can actually request not only the group membership.
Or it could also be that you request an account definition. Because it's very important to understand that the Safeguard is really a target system. It's a target system with a very comprehensive permission model. But it's still a target system.
So if we can go back on the left hand side here, we can see on the basic configuration that I do have account definitions configured here. Now, depending on what kind of PAM user it is-- is it a local user or is this a user that is a Directory user inside the PAM-- we can have different account definitions.
Now, if I look at this particular list, the one called PAM Safeguard local user, I can see that there are some employees who have this account definition assigned to them. And, hence, they will have access to that PAM Safeguard appliance.
If I click, for instance, on this guy called Petri here, I can see that he has an Active Directory account again. He also has the Safeguard. But he's also PAM user, of course.
If I click on his account, I will see that, well, he has more than one PAM user group membership. He's also in the Linux admins and the users allowed to request passwords.
So this was a very quick overview on the integration between Identity Manager and Safeguard.
We are now going to take a look at the connector configuration in the PAG module. Included in the PAG module is, of course, a connector. And the connector is Wizard driven. So you do not have to understand anything about the scheme or anything on the PAM side.
The only thing to remember is that the connector does not use a user ID and a password. It uses a certificate-based authentication. So it means that you have to have a certificate.
And the job server that has the role of connecting to your Safeguard appliance cannot use the local system account when it runs. It needs, actually, that Windows service needs to run under a user where you have installed that certificate in the user's personal certificate store. And, obviously, the Safeguard appliance needs to trust that certificate.
In my demo lab, I have already connected to a Safeguard appliance. So if I click on the target system here, and if I click on the Edit Connection, as you can see that the only thing I provide is the hostname or, in this case, the IP address of the appliance, and the thumbprint from the certificate. I've also checked this to ignore SSL connection errors.
Now anyone who's played around with the synchronization editor in Identity Manager also know that if you click on the Browse on your target system, it actually connects to the target system to show the data on the target system in real time.
And as seen here, it's not only a couple of schema types that we synchronize. It's not only the user and the user groups. That would be the case if the integration was simple. But the integration is really comprehensive. So we synchronize a lot of different [INAUDIBLE] classes of schema types.
Now if I click on User here, it will actually connect to my Safeguard appliance and grab the list of existing users. And as you can see, you remember from previous session, we had a user called Julia Becker. So this is the information in real time grabbed from the PAM appliance where we can see the username. And we can see some information about her on that target system.
You do not have to know anything on how to map between the Identity Manager and the Safeguard because the mapping is also done from a schema and a Wizard inside, and a template inside the connector itself.
So as you can see, if I, for instance, click on User and open up that mapping, I can see on the target system the appliance side and how we map things to a table inside the Identity Manager. Obviously, the PAG module includes a tablespace with quite a lot of different tables in order for us to represent not only users and their group memberships, but also things like entitlements and request policies and so forth.
We are now going to take a look at some of the management you can do from Identity Manager once you have connected to your Safeguard appliance. I'm going to launch the Manager tool.
The Safeguard appliance is really a target system from the identity management perspective. Which, of course, means that you can provision users and you can provision groups and group memberships.
As with all target systems, we do that by defining account definitions. So I'm going to open up the Privileged Account Management menu again here. And I'm going to go to my basic configuration data and open up the account definitions.
Now, I have a couple of existing account definitions already. So I'm going to open up one called the PAM Safeguard local user. That's just a name I gave to this account definition.
The account definition itself, if I opened that one up, obviously, it talks about what kind of target system it is. And, of course, it is to safeguard SPP here in this particular case. I also say that the Manage Level is going to be fully managed.
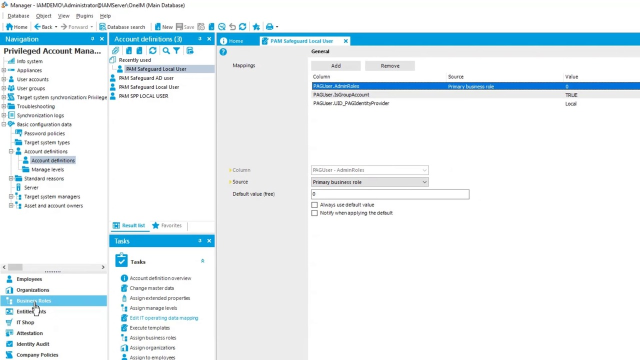
Now, very important here is, of course, the ability to edit the IT operating data mapping. So if I look at that, what I've done here, I have actually said that, well, first of all-- And this is something I haven't mentioned already. But not only can we create PAM users and provision and deprovision PAM user from Identity Manager, we can also provision what kind of administrative roles they should have inside the PAM appliance.
In my demo lab, I've based those on the primary business role. Obviously, I don't think I have that many of those primary business roles configured. But again, I can base it on that. There is group account. By default, I set it to true, because I want inheritance to work for any user created by this account definition.
And the final and most important one is that the account I'm going to create is a local account inside the PAM appliance. Obviously, you can select the directory user account as well as on the PAM side. But this particular account information is for local users.
So if I look at the overview again, of course, I can see that this local user account definition also exists inside two system roles. I can also see that there are some employees who actually have this account definition assigned to them. One of them, of course, is this lady called Julia Becker that we talked about previously.
So, typically, I can take and just randomly grab an employee from my list here. I go down here and I take, for instance, Ben Follin here, for instance. If I want to give him just an account in the PAM appliance, I can just simply assign an account definition for him, of course. And then I can say I want him to have a Safeguard local user, for instance, a PAM Safeguard local user.
If I save this now, in the background now, provisioning event will occur. And this individual, Ben Follin will be provisioned to my Safeguard appliance. If I open up my job queue monitor here, I can actually see that it's [INAUDIBLE] the event, that is found that there is an account definition that needs to be assigned to it.
So now that is running inside the database first. And once that has been executed, it will also jump into the actual ad hoc provisioning. And that happened right now. It would connect to the PAM appliance. And it will create the user, the PAM user account for Ben Follin
Now, that doesn't mean that Ben Follin can do anything inside the PAM platform itself. It's actually just the user account being created. Not the fact that Ben could do anything inside the-- as you can see, it's processing right now.
So once this one is finished, I can actually go to my Safeguard console here. And as you can see, items have been modified. So please press the Refresh. I'm looking at the users inside.
And, as you can see, Ben Follin now has been created inside my Safeguard appliance. As you remember, it is a fully managed account. So I will grab the first name, last name, the work phone number. If I look at the location, well, that's actually the time zone for him.
He has no specific permissions inside the appliance itself. He's not an administrator of any kind. And the authentication local, of course. So now we can log on to the PAM appliance, but he can't really do anything because Ben has no entitlements inside the PAM platform.
I go back to my Privileged Account Management. I look at my user account. And I take this newly created one, now, that Ben Follin. Of course, I can assign him to a user group.
And the user groups I will see here is user group that happens to be local user groups. The two groups you see that are grayed out here on the screen, they are synchronized into the Identity Manager tablespace. But they are really Directory groups inside the PAM appliance. And I cannot assign a Directory group from here, because it is a local user. It needs to be a Directory group user in that case.
But I can give him, for instance, let's give him the group memberships call the users allowed to request password. If I save this now, the provisioning event will happen in the background, of course. And if I double click on him now, I can now see that he has a PAM user group membership.
Now, obviously, it needs to be a provision in the background. It's happening right now in my demo lab here. It can take a couple of more seconds. But as you can see, the ad hoc projection is now about to be executed in the background now.
So if I wait for a couple of more seconds, and I just wait for the processing to stop. I minimize my job queue monitor, bring up my Safeguard console again. And I need to refresh the list again. And I click on Ben Follin. And as you can see now, on Ben Follin, now has one group membership. And if I look at the group, he is now a member of the users allowed to request password.
You can do this in very nice and proper way, of course. You can publish the ability to request access and request access to the PAM appliance itself, including what you're entitled to do inside that PAM appliance. And, obviously, you can have an approval workflow assigned to that so no one can have access to the PAM appliance unless the appropriate people approves it.
As I mentioned earlier when we talked about the account definitions inside a Privileged Account Management module-- and you remember when I showed you the account definition, the Safeguard local user, and the IT operating data mapping for that one. The first one I had here was that, based on your primary business role, we will match the admin roles inside the Safeguard appliance.
Now, admin roles inside Safeguard appliance is really the permissions. If I bring up the Safeguard appliance again here, and I click on, for instance, Ben Follin here, and we click on the permissions. As you can see, he's just a user. He's not responsible. He's not an authorizer. He's not a user manager, help desk, or appliance, or auditor, or anything like that inside the PAM appliance itself.
But I've configured it so we can use a primary business role to determine if you should have permissions inside the Safeguard. So what I have on the business roles in inside my-- I have a couple of PAM roles here. For instance, the PAM Auditor. It's a business role called PAM Auditor. And as you can see, there is one user that has this as his primary membership.
And I have configured some IT configuration settings on this business role that relates to Safeguard. So if I open that one up and take a look at it, so what I've configured here is that the admin roles should have the value of 32.
Now, this is a bitmask configuration. So you need to calculate what the value should be for those different-- as you remember, if I bring up this tool again, and I bring up this user and look at permissions, these are bitmaps based. So 0 means that you have no permissions at all. And 32 will actually be the auditor roll.
So, again, if I go back here-- and so, by assigning the PAM Auditor as a primary role for a person who also has a PAM account, they will be an auditor inside the Identity Manager. So if I look at this particular individual, now the employee Pekka Ruippo-- it's a Finnish guy. His user ID is PEKKAR_ADM, because it is really a sub identity to this main identity inside Identity Manager. This is just a way to model it, right?
Now the sub identity PEKKA_ADM here, he has a PAM user account. And that user account comes from that same account definition as the PAM Safeguard local user. But the primary business role for him is a PAM Auditor.
So this is just a way, again, I'm using a sub identity in this particular example. But it could be a main identity, of course. If you assign one of these roles, you will also get the appropriate permissions inside the PAM appliance itself.
So if I look at his account inside the PAM appliance, the Safeguard appliance, and if I find him here, he's should be somewhere down here, PEKKA_ADM here. I open up his account.
The Safeguard doesn't know that this is a sub identity. It's just an identity, right? But if I look on permissions, as you can see, he's now an auditor. So you can control the permissions by, for instance, using business roles inside the Identity Manager.
Up until now, we have looked how we can connect Identity Manager to a Safeguard appliance. We have also looked on the ability to create PAM users from Identity Manager, and also how we can assign group memberships, which could mean that they also have entitlements inside the PAM appliance itself. So the PAM user can, for instance, request password releases or sessions or something like that.
Now we also saw how we can control the administrative roles inside Safeguard from Identity Manager. And we did that by adding it to a business role inside Identity Manager and assigned that business role as a primary role for one of the users. And that made him an auditor inside Safeguard.
Now we're going to take a look at the governance part of the PAG module. And to do, we are going to log on to the web portal as one of the super users in this demo lab.
Now this individual, Ben Paxton, he has a lot of roles inside the Identity Manager. And one thing he can do, he can create a new attestation policy. Which means that it's possible, then, to launch a campaign where someone needs to attest something that has to do with Safeguard.
So he's going to click on the attestation governance administration and go to attestation policy settings. Now, for demo purposes, I'm going to create a new attestation policy. We need to give it a name. So I'm going to call it PAG demo.
Whenever you create a new attestation policy inside Identity Manager, you need to select an attestation procedure. So you click on the Assign button here. And since we now have the PAG module installed, this privileged access is now available for us to choose from. So I'm going to open that one up.
Now as you can see, there is multiple things to choose from here. Now, the one that I'm going to select is the PAM access attestation, which literally means that we're going to attest what PAM uses are entitled to do in the PAM appliance. The other ones are saying that we can attest the fact that this account should exist, or this asset should exist, or this Directory account should exist, and so forth. But I'm going to select the first one here.
And, as whenever you create an attestation policy, you need to select which approval policy that applies to it. There is only one to choose from here out of the box. And that's actually going to use-- the attester is going to be the target system owner. Now, I have a target system owner defined in my demo lab.
And the fourth thing you need to select here is a schedule. Now, I have created a schedule called PAG demo monthly. The reason why I created a separate schedule is because then I can just start that schedule. And the attestation campaign will launch. So I'm going to select this PAG demo monthly. It's just a schedule created from the manager tool.
Now, time required is obviously how many days do we give to the attesters to actually perform the access review. And seven is the default, so I'm not going to change this one here.
Now, the final thing you have to do when you create an attestation policy is to select a condition. What are we really going to select from the PAM access attestation in this case? So I'm going to click on the plus sign here. I'm going to select-- now we have obviously different conditions types to choose from. We can select all PAM access. That means every PAM account or PAM user account and whatever they are entitled to do, we can attest.
But you can also choose, for instance, for a specific-- with a matching name or defined risk level or only specific employees request type. That is, if I choose this one, then I can say OK, I'm interested in PAM users who are allowed to do password releases and remote desktop, for instance. But the one I'm going to select for simplicity is all PAM accesses. So I select that one and press OK.
Now, if there are no matching objects once you have selected a condition down here, you'd better do it again, right? But I have 24 matching objects. If I click on it, I can see that, well, there's obviously people who have some access to password, to Linux, and some may have some remote desktop accesses and so forth.
So, I'm happy, actually. So I'm going to create this new attestation policy now. Now it appears here, as you remember, I called it PAG demo. It's not running. As I said, I selected a custom-made scheduler here. So I'm going to open up the manager tool. And if I go to attestation, and I go to basic configuration data, I can see my schedule I just created called PAG demo monthly.
One thing to remember when you do this yourself is that when you create a new schedule, because you want to start the schedule immediately. I'm going to actually do that while I speak here. So don't forget to check the box Enabled. Because if you don't do that, nothing's going to actually be able to run.
So now I can say that the PAG demo policy is actually part of this schedule. And in the background now, there's a lot of things going on inside my Identity Manager because the schedule launched. And now it's going to create the attestation cases for this attestation policy. That's going to happen in the background now. So I have to wait for a couple of seconds for that to actually appear.
As you can see now, it calculates the things in a short while. Now the attestation policy will execute. And once that's been executed, whoever it was that was the target system owner is going to be prompted, typically notified by email. And then after that, he or she needs to actually go in and perform the actual review.
Now, if I go back to the web portal again now and I click on the Back button here, and I go to my policy runs, I will see that the PAG demo is actually running right now. And it is in a good state. Because it was launched today and seven days from now it's going to expire. I can see that there are 24 decisions to be made. And I can click on the Approvers tab. And I can see, OK, it's this individual that needs to perform this task.
So typically what I will do, I will open up another web window here. And I will log on as this individual. She is a lady who is the target system owner of the PAM appliance. It's her job to actually perform the access review.
Now, once she logs in, she will be notified of course with an email. But once she can read the email, you can see she got 24 pending attestation. 24 decisions to be made here. She can click on that one. And they will appear on the screen for her. If I maximize the screen here, it's easier, perhaps, to see.
So there's a lot of decisions to be made here. But if you look at it closely, you can click on the first one. You remember Ben Follin, that's the guy we created earlier in a previous session. He's obviously allowed to request a password for the privileged account Linux admin on the privileged system Linux server.
So, obviously, I can see exactly the details on the right-hand side. So it's Ben Follin. He can request password for the Linux admin account on this particular--
And now I can start making my decision. Yeah, I think he should. And it's probably OK that he can grab the root password as well. And this is a cumbersome job, of course, to make all these decisions. But that's part of access reviews, regardless of what it is.
Now I'm going to be really lazy. I'm going to say it's OK for everyone. Now this button, Select All, Approve or Select All, Deny, that's something you can, if you like, take away by a configuration option. Because some of our customers, they don't want the attester to be able to Select All, Approve or Select All, Deny.
I'm actually going to look at all the decisions here. So I'm going to Select All for all 24. And this is no difference for any-- I can say All is OK. And I can say my decision.
Now, obviously nothing's going to happen now. But what we have done, we have showed that we can have this deep insight into the Safeguard PAM appliance from Identity Manager.
The last section, we're going to cover in this PAG module is the ability to use the IT-shop capability for the PAM users to request a password release or a session release.
Now, the first thing I'm going to do in this demo lab environment, I'm going to go to the Safeguard, that page, and log on with the user Julia. You remember Julia Becker. And when she logs on to the web portal of Safeguard, as you can see, there is no available request or approvals or anything. It's absolutely empty on her page here.
Now, with another browser, I'm going to log on to the Identity Manager. I'm going to actually move this a bit slightly to the right here. So you see that in the background there. And I'm going to log on as Julia here as well to the Identity Manager portal.
Now, as you remember, she is a PAM user. And she has the permission to request password releases. So she clicks on that and start a new request inside Identity Manager. And there's some built-in functionality in the PAG module called Privileged Access Request. It's a service category that you can select from.
And the thing that she's going to request here is a password access request for a password release. So she simply clicks on Add To Cart here. Now, obviously, she can select for another PAM user account. But it's her user account here. And she needs to select, OK, what system? What asset am I interested in?
And the thing that's going to be listed here are the things that is available for her. And the only thing that's available for her is this Linux server. And the second thing, of course, is to select OK. You want to request a password release for an account. So she also needs to select which account.
As you may remember, she is entitled to request the password for both the Linux admin and the root accounts. She's going to select a Linux admin account in this here. She could always, obviously, add a comment to it. And she can also, of course, make the request to happen in the future. But she's just going to select the Linux server and the Linux admin account and press Save.
Now, once she submit that request, since it's done inside the Identity Manger, there might be an approval workflow associated with this request. So she could look at her request history here in the background. As you can see, she requested a password release, and it is in request state. If she looks into the workflow here, she can see, ah, it needs to be approved by Lisa Svensson. As you remember, Lisa is the target system owner for the PAM appliance.
So typically what happens in Identity Manager is that Lisa gets a notification. There is a pending request for you. So Lisa logs on to the portal. And when she comes in, she can see there's one pending request for her. So she goes there.
And she can say OK, about a minute ago there was a password release request from Julia Becker. She can see the details, of course. It was a password release. She can click on the previous-- actually, you can see that it is Linux admin account. And she can take a decision. I'm going to say yes to it, she says.
So she's going to approve this decision. And she can obviously, say, put a reason or something for now, for instance, and save her decision.
Now, in the background right now, what's going to happen if we'll look into the job queue is that, since it's now being approved, this request. So going to connect to the PAM appliance to create the actual request in the PAM appliance. Because if this was not approved, it's not going to ever reach out to the PAM appliance. So now it's actually happening.
And as you see in the background here, something happened there. Oh! There's one available request. So I can click on that one. And guess what? Now I have the password being available for me for the Linux server within Linux.
So now I can actually reveal the password. And obviously, also, of course, copy this password. And copy it into a SSH terminal and log on to that Linux machine. And this ability to use the Identity Manager IT-shop structure to publish these things is something that you get out of the box for the PAG module.
And that summarize the things that I wanted to show you regarding the PAG module. Thank you everyone.
 34:08
34:08
