Hi, this is Joe Campbell, principal solutions architect at Dell Software. And in this two-part video series, we're going to be taking a look at what I like to call making authentication smarter. In particular, we're going to be using the Cloud Access Manager product to do simple authentications. And we're going to find that some of the applications I have secured are using multi-factor authentication.
Now, that's great for a lot of the use cases that our customers want to see. However, we're going to present an alternative to the traditional implementation of multi-factor authentication in what we refer to as an adaptive-authentication engine or using our risk engine.
So let's take a look at exactly what I'm talking about. So how do people typically handle multi-factor authentication? Well again, let's look at a really traditional scenario-- a user connects to a secured application. They're given the two-factor prompt. They generate a key. They enter the key. They use the app.
They close their browser. They go access the secured application again. They're given a two-factor authentication prompt. They generate a key. They enter the key. They use the app. They close the browser.
And this basically continues over and over and over again, every single time someone tries to connect to that secured app. And what we're asking is, is it necessary that we have to do this every time? And a lot of our users don't think so.
Well, what do we know about this user when they connect? Let's take this user here. He connects to a secured application. We see his IP address. We see the time of day, maybe, that he's coming in-- maybe business hours, or maybe it's always around 10 o'clock at night. We see the type of browser he's using and the browser that he's using, and we see the application that he's asking for.
Well, what about the next time this person connects? Well, we see his IP address. Nothing's changed. We see the time of day he's connecting. Nothing's changed. We see the browser he's using to connect. Again, nothing's changed. And finally, he's connecting to the same application he was before.
The moral of the story here is that nothing's changed. What if we could pay attention to the fact that nothing changed and use that to make authentication decisions more intelligently? Well, the security analytics engine, what we refer to as the SAE, was introduced in version 8 of Cloud Access Manager. It enables risk-based authentication in Cloud Access Manager. We make intelligent, real-time authentication decisions based upon a number of factors. We're going to get into that a little bit later. And really, we implement two-factor authentication elegantly, not with a hammer.
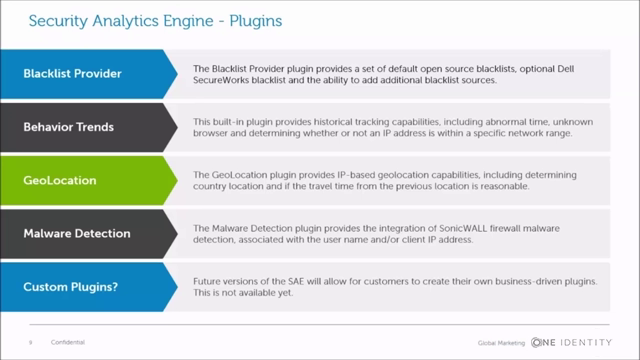
It's built on a plugin architecture. So let's take a look at that plugin architecture. We ship out of the box with a Blacklist Provider. And you can see what it says here-- the Blacklist Provider plugin provides a set of default open source blacklists, optional Dell SecureWorks blacklist, and the ability to add additional blacklist sources. And the demo I'm going to show in the second video, you're going to see that in action.
Behavior trends-- we mentioned things like IP address, time of day, the location I'm connecting from, the browsers that I'm using, et cetera. Basically, we take all those behavior trends about an individual-- I mean, we're looking at a specific person. And we're saying, has anything changed? Take, for instance, a person who connects from home every day in that little circle diagram that we saw before. If none of those behavior elements have changed, then maybe we can draw down our multi-factor authentication and let that person through without a multi-factor challenge.
But then that person takes his laptop, drives over to a coffee shop somewhere. What changed? Well, the IP address changed. Everything else remains the same. That could come into our system and be seen as a risk, that something about this person's location has changed.
What if the location change is even greater than that? We have a geolocation plugin. This one I find particularly interesting. And basically what it says is, I see you logging in from San Francisco today. And then five minutes from now, you're logging in from Dallas. Well, we actually calculate the reasonable time it would take for you to travel from San Francisco to Dallas. And if it's five minutes, I can tell you that's not reasonable. So if it's something more along the lines of eight hours, maybe that's reasonable. So even though that's going to come through and be seen as a risk in our environment, something that you can respond to intelligently.
Malware detection-- we have an integration with our SonicWALL firewall clients. SonicWALL is going to say, I've identified certain computers on the network that are either malware hosts or I see virus signatures coming from this machine. Maybe it's trying to contact the mothership, etc. That's going to get picked up by the SonicWALL appliance, and SonicWALL is actually going to tell my risk engine when this person tries to connect, hey, this person's already been identified on the network as a threat. And again, we're going to respond to that elevated risk intelligently.
And finally, what about custom plugins? In the current version, we don't support custom plugins. However, it is on the roadmap, and it's something we do want to support. And why is that relevant to you? Well, take, for instance, a financial company-- someone on the stock market, let's say. And they want to build a risk profile based upon the fluctuation of the stock market.
Well, that's not something we have built in today. But that's something that that company may want. Or maybe it's a military organization, and they want to elevate the risk based upon the current DEFCON status. These are things that are business-specific risk drivers. And when we implement the support for custom plugins, our
 07:31
07:31
