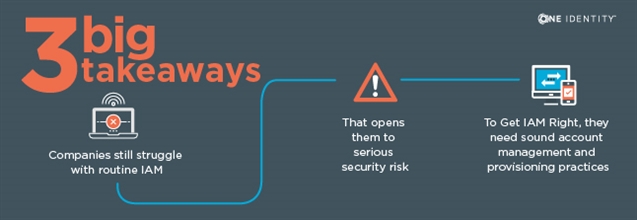
The traditional perimeter is eroding due to the mass adoption of cloud computing, the proliferation of SaaS applications, and a major rise in the number of identities — both human and non-human — that businesses are now required to secure. To learn more…