Innovations and Integrations
Behavior Driven Governance (BDG)
One Identity Manager 9.2
Behavior Driven Governance provides organizations continuous visibility into what access rights are being used, if in use at all, and by whom.
Behavior Driven Governance enables organizations to easily enforce the principle of least privilege and reduce vulnerabilities, recertification fatigue and licensing costs associated with underutilized resources. In addition, Behavior Driven Governance assists administrators and application owners with notifications and actions related to entitlements that are rarely or never used. This out of the box feature strengthens security and compliance adherence and reduces administrative workload and costs.
Behavior Driven Governance allows you to:
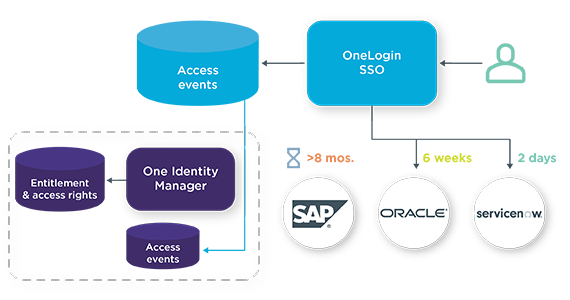
- Use access insights in OneLogin to inform governance policy decisions in Identity Manager
- Analyze access frequency and user location from OneLogin to automatically determine access rights & entitlements in Identity Manager via policy
- Recommend removal of unused entitlements to reduce vulnerabilities
One Identity Manager evaluates event data, including application access frequency. One Identity Manager correlates any associated accounts and entitlements and, using an attestation, provides the user's manager or responsible party with the opportunity to revoke access deemed unnecessary due to lack of application use.
One Identity Manager 9.0
If you are using One Identity Manager 9.0, you will require a Solution Accelerator, accessible via GitHub, to enable Behavior Driven Governance.
Just-In-Time (JIT) Privilege
One Identity provides Just-In-Time (JIT) Privilege that combines the powerful Active Directory (AD) Management capabilities of Active Roles with the unmatched password management capabilities of Safeguard to significantly reduce the risk of cyberattacks on privileged accounts. One Identity Just-In-Time (JIT) Privilege provides privileged access to Active Directory (AD administrators only when necessary. When the account is no longer in use and is signed back in, JIT Privilege disables it and removes it from all privileged groups. The solution then changes the account’s password. This least privilege approach to AD access protects accounts from compromise. JIT Privilege technical details can be found on GitHub.
- Apply Zero Trust least privilege philosophy to AD privileged accounts only
- Ensure that privileged permissions are only available and assigned at time of request
- Revoke privileged permissions where they are no longer required
- Disable accounts when not in use
Privileged Access Governance
One Identity provides Privileged Access Governance (PAG) as an out-of-the-box module in Identity Manager that can integrate with Safeguard. Privileged Access Governance closes the gap between privileged access and standard user identities across the enterprise. It also protects and manages privileged access and grants a 360-degree view of users, accounts and activities. This integration module connects Identity Manager with Safeguard and provides enterprise provisioning and deprovisioning, access request and approvals, delegation of roles and responsibilities, policy/SoD detection and enforcement and attestation/certification of access.Provisioning and deprovisioning Access request and approvals
- Delegation of roles and responsibilities
- Policy/SoD detection and enforcement
