Welcome to video two of the Security Analytics Engine walk through and demo. In this video we're going to walk through a couple of scenarios that really show the features of the Security Analytics Engine and to do that I'm going to go over to my virtual machines and start with basically the user experience of getting access to an application in Cloud Access Manager.
So I'm just going to fire up my browser. There's no multifactor authentication configured currently on my login. But what I have done is configured it for the application, you're going to see right over here. So for these applications I should be able to connect to them and get access just fine. Here I am logging in, no problem. Form fill, we can try the header injection example. Works just fine. And we can even try something Federated like Google Apps. And again we're in just fine.
So what happens, though, when we connect to an environment that's secured for multifactor authentication, like this one. Well let's hit it. Boom. We get a multifactor authentication prompt. So what I have to do now is go get my token. Login. Get a new response, come over here, paste that in, and now we get the web page.
The point I was making before, in video one, is that if I shut my browser down now the session cookies are gone. And when I try to do this scenario again I'm going to be prompted again, and again, and again, every single time I click on this. Right now, of course, it's going to go in because I have a valid session. However, if we kill the session and come back in-- let's just go ahead and drive that point home. Click on it again-- and there's my multifactor prompt again.
So right now essentially what we've done is we've turned on multifactor authentication and we've assigned it to a specific application. There are variations of how you can do this in Cloud Access Manager. We can say only external users are going to have multifactor authentication. All users are going to have multifactor authentication. We can assign it to a specific application, and we can even say only users of a specific role have multifactor authentication. But again, we're not using a risk based approach. So every single time those particular users hit the exact same site, under those circumstances, they're going to get that multifactor challenge every single time.
So let's turn off multifactor authentication and instead turn on the Security Analytics Engine. To do that we're going to close this down, and log into the admin interface. We're going to go to the settings. And you'll see this new option called Externalized Access Control. Click on that, and you can see "Route Access Manager will manage the step up authentication decisions"-- that's what we want to change. We're going to say the Security Analytics Engine will manage those decisions.
When you do that you see the defaults pop up at the bottom of the screen here. For instance the low risk user setting is currently from zero to two. You can see where I can change that. Medium risk is three to five, just like in the presentation in video one. If we scroll down a little bit more you can see, this is what we do with a low risk user, this is what we do with a medium risk user, and this is what we do with a high risk user. OK?
So these are the global settings that are set. Let's just go ahead and save that, and then go back and take a look at the application we were testing before. So that's in here. And now we'll see that where we used to see multifactor authentication choices we see instead threat levels. Right now regardless of the threat it's going to say I'm going to allow access for low risk users, I'm going to allow access for medium risk users, and I'm going to allow access for high risk users. So we're going to change. We're going to say high risk folks are going to be denied, medium risk users are going to be doing a step up authentication.
So if I wanted to I could say, this is an ultra sensitive application and unless you're a low risk user I'm going to deny you completely. What we're showing here is essentially the global policy can be overridden for a specific application. But I'm going to go ahead and stick with the global policy or at least make it seem the same and we're going to click Save.
So now we can minimize this and go back over to our user. And because our user is essentially considered a low risk user at this point when we click the basic authentication link we can see he gets right into the application. So there's no multifactor challenge here because in my lab environment I've already built a profile for this user. I already know which IP he's coming from, the time of day he's coming from, geographically where he's coming from etc.
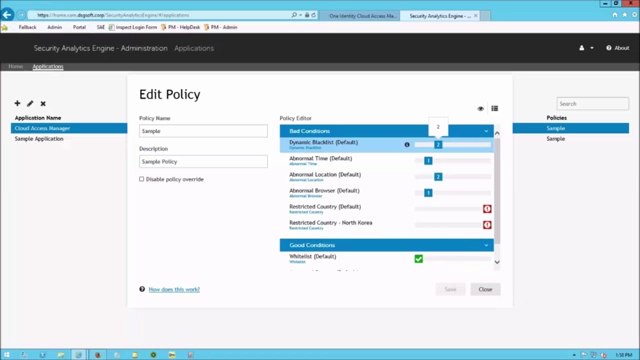
So let's show what happens when the policy is actually kicking in. And to do this we're going to go to a machine on the network that's basically been identified as a threat. So let's go down and launch the browser. Login. And we sail right into the portal, which isn't exactly what I would expect if this machine was on our blacklisted server. So let's go back and take a look at the policy and find out why. Over here is the Security Analytics Engine interface and we're going to go over to applications. Select Cloud Access Manager and edit that application. We can see the policies down at the bottom. We'll select the current policy and edit that.
And here's where you can see the blacklist. Oh I see, so blacklist is only generating a
 10:35
10:35
